While Zoom has proven to be an excellent tool for collaboration across WCM, we’re facing a new threat called “zoombombing”. Malicious parties are finding Zoom links – sometimes just guessing random meeting IDs – and joining meetings to disrupt them, often with offensive materials. This problem is not exclusive to Zoom – all online meetings can be compromised if not properly secured.

If you are hosting Zoom meetings, it is important that you secure them to reduce the risk of Zoombombing. See the below recommendations for steps you can take to secure your meetings, both before they happen and while they're occurring.
Don’t share your Zoom links publicly: Sharing a Zoom link on social media, your departmental website, an open Google Document, or the WCM Events Calendar makes the meeting open to anyone in the world.
Consider sharing links via direct email or collecting RSVPs instead. Zoom has a built-in registration system you can use to gather RSVPs and automatically share meeting details.
Set a password: You can easily require a password to join your Zoom meetings. With a password set, you can share the meeting link with ease but only share the password with people who are meant to attend.
Disable “Join Before Host”: The ability to join before the host can be disabled to ensure the meeting only starts when you or a co-host arrive. This can prevent someone arriving before you can monitor the meeting.
Set a back-up host: When creating a meeting, you can set “alternative hosts”. Hosts and co-hosts have special rights (detailed below) that allow more control over what’s happening in the meeting. (See During Your Meeting below for what hosts can do.)
Use an authentication profile: Are all your participants from WCM or a common affiliate? You can limit entry to just those institutions by using an authentication profile.
Consider using a waiting room: If you want to review participants as they’re joining, you can make use of a feature known as the waiting room. This allows you to vet participants before they’re admitted to the meeting.
Always sign in: If you have the desktop Zoom client installed, make sure you’re signed into your WCM account. Joining meetings without signing in prevents you from having host permissions for your meetings. Without a host, you will not be able to control what happens during the meeting.
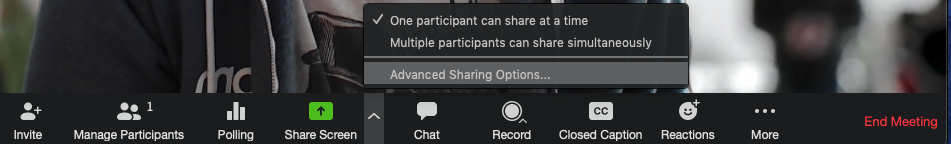
Limit who can screen share: As host, click the arrow next to “Share Screen” and select “Advanced Sharing Options”. You can then limit screen sharing to “Host Only” if you don’t know all the participants. Need someone else to share? You can make them co-hosts on the fly from the Participants list.
Review your participants list: By clicking the “Manage Participants” button, you can see who has joined your meeting. See someone you don’t recognize? Ask them to identify themselves, so you know you’ve got the right people in the meeting.
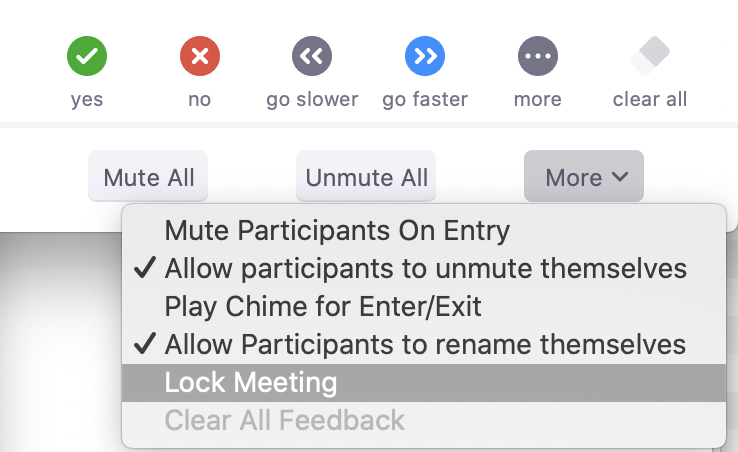
Lock the meeting once everyone’s arrived: If you’re not expecting anyone else to join, you can lock the meeting. This can be done using the “More” menu in the Participants window.
Know how to handle a disruptive participant: If you’re a host, there’s a lot you can do to manage a disruptive participant. Below are instructions on how to:
Adapted from Zoom’s How to Keep the Party Crashers from Crashing Your Zoom Event