
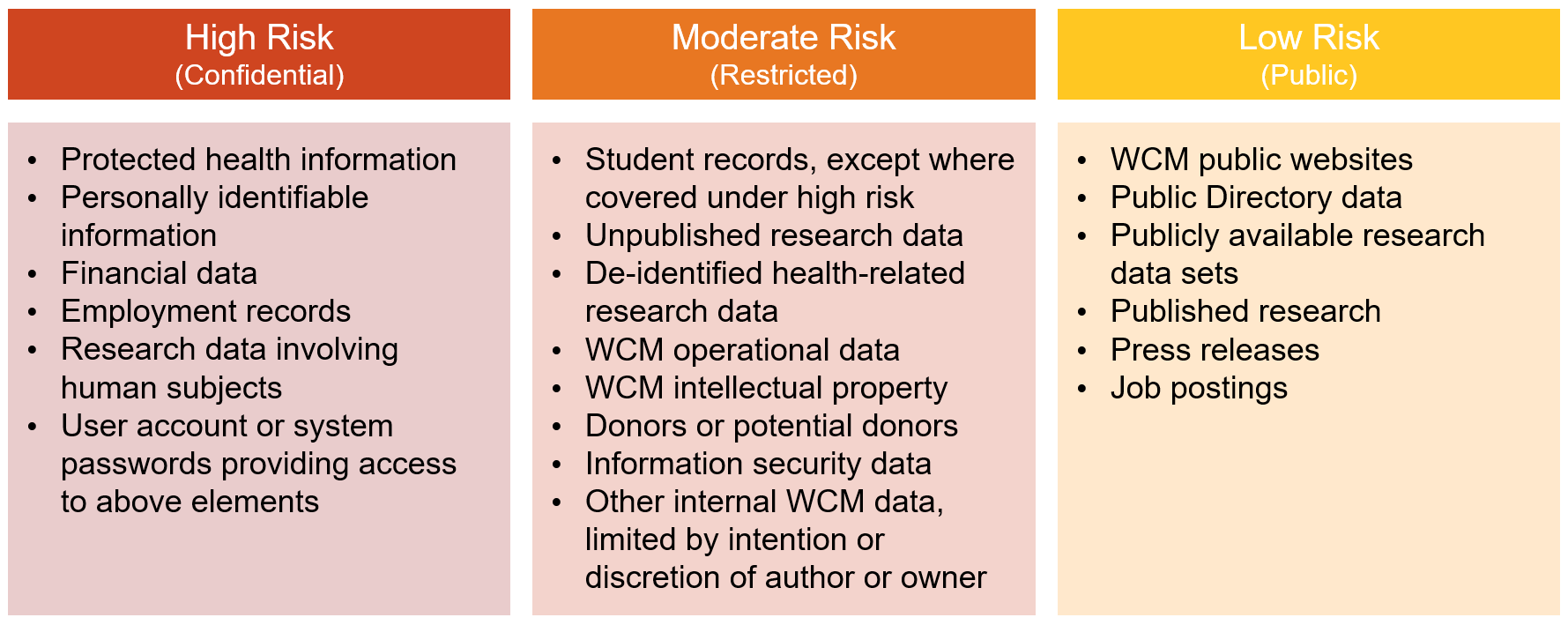
Can I use my domain name that I purchased?
Fully qualified domain names can be used, but with two conditions:
See 11.16 Domain Name Policy for more information.
Are there other content management systems that we can build our website on?
Drupal has been selected as the content management platform for WCMC.
If I build my website myself using a website builder, will ITS support it?
No. Websites doing official college business must be built following the official college website standards.
What support is offered for the website following launch?
We offer a wide range of day-to-day business services to help maintain, optimize, and tune your website as part of your business plan. See the Web Maintenance service for more information.
We have a website design ready, can someone there build it for us?
Websites built for official college business must adhere to design standards as defined by Digital Engagement and External Affairs. Please contact the Digital Engagemeent team for further details.
What if my website shares branding with NYP?
Joint initiatives and units that are housed administratively within the College can have websites developed by ITS. Joint initiatives and units that are housed administratively within the Hospital should contact NYP Marketing for web site projects.
What's the minimum amount of computation that can be purchased?
Right now it's a core-year, designated as 8585 core-hours. The cost is $400 per year.
What is the Weill Cornell Medicine password policy?
Please refer to our Password Policy for more information.
What if I forget my password and the answers to my private questions?
You can call the ITS Service Desk at 212-746-4878 to have your password reset using additional steps.
What is the maximum file size I can email as an attachment?
The maximum file size is 25 MB if you are sending the attachment via Outlook or Webmail. To send larger attachments up to 35GB, use the File Transfer Service.
What is Focused Inbox?
Focused Inbox helps you focus on the emails that matter most to you. It separates your inbox into two tabs—Focused and Other. Emails you need to act on right away are in the Focused tab, while the rest wait for you in Other. You can switch between tabs at any time to take a quick look.
Focused Inbox is available to all Office 365 customers using the Monthly Channel of Office 365 ProPlus, in Office 2019 for Windows and Mac, and in Outlook for iOS and Android. It replaced the Clutter feature in Jan. 2020.
Visit the Microsoft website for more information about using Focused Inbox.
How do I get my smartphone registered?
We put together a couple of step-by-step guides to help you register your phone:
Do I need to take HIPAA training?
Training in the Health Insurance Portability and Accountability Act (HIPAA) is required for all WCMC employees, regardless of whether your work is patient-related. When you begin your employment at WCMC, Human Resources will indicate how you can take HIPAA training in WTMS. This training must be completed within the first 45 days of your employment. Please note that all Weill Cornell employees, regardless of how long they have been working for the institution, may be asked to retake their HIPAA certification when updates are made to the policy. Your department will be notified if you are required to retake the certification.
How can I add course content in LMS for others to see?
Training Administrators and instructors can upload and administer course content in LMS. If you require this access, please contact its-training@med.cornell.edu for more information.
What courses are available in LMS?
There are dozens of courses in the WTMS course catalog. You can view available courses by logging into the Weill Business Gateway and clicking the "My Workspace" tab. Once there, you will find a link to "Learning" and be able to search the entire course catalog to view all course offerings.
What is MobileIron?
MobileIron is a mobile device management (MDM) system that provides ITS with a means of governing mobile access to WCM resources, including email, calendar, contacts, and other central applications. Through the use of MobileIron, which is a free application that is installed on a governed mobile device, ITS has the ability to configure devices with the appropriate WCM settings to allow access to Wi-Fi networks, a WCM email account, and WCM applications. As a benefit to both WCM and the end user, MobileIron helps manage compliance with security policies and other regulations by enforcing device encryption and the use of a passcode to reduce the risk of accidental or improper disclosure of data In the event the device is lost or stolen.
Is MobileIron required for my mobile device?
Yes. Any mobile device (smartphone or tablet) configured with a WCM email account (or wishing to access the WCMC Wi-Fi network) must have MobileIron installed. Without MobileIron, WCM cannot ensure the security of all devices with WCM data. In the event the device is lost or stolen, there are no assurances that WCM data has not been breached or inappropriately disclosed. Weill Cornell's faculty, students, and staff create and share a wealth of information on their mobile devices every day, much of which may be confidential. Should your device become lost or stolen, ITS can locate or wipe your device remotely at your request to make sure this data never gets into the wrong hands. Even if you do not regularly work with confidential data, it can protect the other content on your phone and is necessary for inventory tracking by your department. Not only does it protect you, it protects everyone who does business with Weill Cornell.
But I don't access clinical or confidential data. Do I still need MobileIron?
Yes. WCM's definition of confidential data extends beyond protected health information (see ITS 11.03 - Data Classification). If you use your mobile device to access the WCMC wireless network, you are using Weill Cornell resources and will need to have MobileIron installed.
Can ITS spy on my mobile device once MobileIron is installed?
No, ITS cannot spy on your device through MobileIron, nor is ITS interested in actively monitoring your device. In addition, ITS enforces very minimal requirements and restrictions on your device – a password, which enables encryption. Here are things MobileIron does not do:
Also, ITS does not read individual emails in your Weill Cornell account, nor can we access any personal email from external sites like Gmail or Yahoo! Mail. ITS uses a data loss prevention software in accordance with College policy (see 11.02 - Privacy of the Network and 11.03 - Data Loss Prevention) to make sure confidential data is not sent to external accounts (those that do not end in @med.cornell.edu) without encryption.
It is important to note that although ITS does not actively monitor emails, Weill Cornell reserves the right to access, review, and release electronic information under circumstances necessitated by legal or regulatory requirements.
I lost my device! What should I do?
If your device is lost or stolen, notify the Service Desk and your department administrator immediately. ITS will work with you to locate your device or wipe any Weill Cornell services to prevent a breach of confidential data. If you are unsure of the whereabouts of the device, it is also recommended that you file a police report with campus security of local authorities.
If my mobile device is remotely wiped, will my personal information also be deleted?
No. If your phone is lost or stolen, ITS will only wipe Weill Cornell services. However, if requested, ITS can wipe the entire device. Contact the Service Desk for more information.
What information does MobileIron collect about me and my device?
MobileIron collects the following information about your device:
What changes will I see on my device once MobileIron is installed?
When MobileIron is installed on the device, a list of "profiles" with configuration settings will appear under Settings > General > Device Management. Among the profiles is an "Exchange Account" setting, which is a configuration profile that sets up your email and appears in the "Mail" app and the "Mail, Contacts, Calendar" settings. The "Password Policy" profile appears under the "Restrictions" area, which enforces a passcode to unlock the device.
The other settings that are deployed include additional features that provide easy access to the network, such as connecting to WCMC Wi-Fi networks. ITS also has some "web clips," which are bookmarks that point you to WCM Emergency information and other helpful internet resources. ITS can also deploy or publish "managed applications," which are applications that can be used for work purposes, such as Box. ITS also have the ability to deploy paid applications, which may occur in the future.
Most noticeably, you'll see two key apps installed on your device, which are described below:
MobileIron: The MobileIron app allows ITS to apply and enforce certain settings on your device to ensure security. You do not need to configure any settings in this app and will most likely not need to access it. However, ITS can use MobileIron to send important messages to your mobile device and suggest upgrades to applications that are relevant for WCM (e.g., Box, Zoom, etc.).
WCM App Store: The WCM App Store is our internal app store, making applications relevant to the WCM community available for download. Some apps will install directly, while others may lead you to the App Store where you can download the recommended application. You can periodically check this feature in the future as ITS recommends more apps to the Weill Cornell community.
MobileIron also changes security settings on your mobile device once it's been installed. When your mobile device remains idle for a period of time, it will automatically lock and require a passcode of your choosing to unlock it. Per Apple's default settings, if you fail to input the correct passcode 10 times in a row, your mobile device will be completely wiped. (If this happens, you would need to input all your information from scratch or restore your information using a backup from iTunes.)
Can I still access the WCMC Wi-Fi connection and my Weill Cornell email without installing MobileIron?
No, ITS requires MobileIron be installed and configured in order to access these services.
Which devices does MobileIron support?
At this time, MobileIron can be installed on Apple iOS devices (i.e., iPhones and iPads) running iOS 11 or above, and Android devices running Android 8.x or above.
How is MobileIron different on an Android device?
On an Android device, ITS configures an Android Enterprise Work Profile which is a secure environment within your mobile device. The Work Profile separates institutional or enterprise data from your personal data. This separation happens seamlessly and is almost transparent to the mobile device user. It also offers encryption and extra security. This not only encrypts institutional data, but it makes you HIPAA compliant, a prerequisite for mobile data and content at WCM.
On your Android:
Important: As a part of security and separation within the Work Profile, items may be brought into the Work Profile but not outside of it. You may delete items within the Work Profile, but you cannot save a secured item outside of the Work Profile.
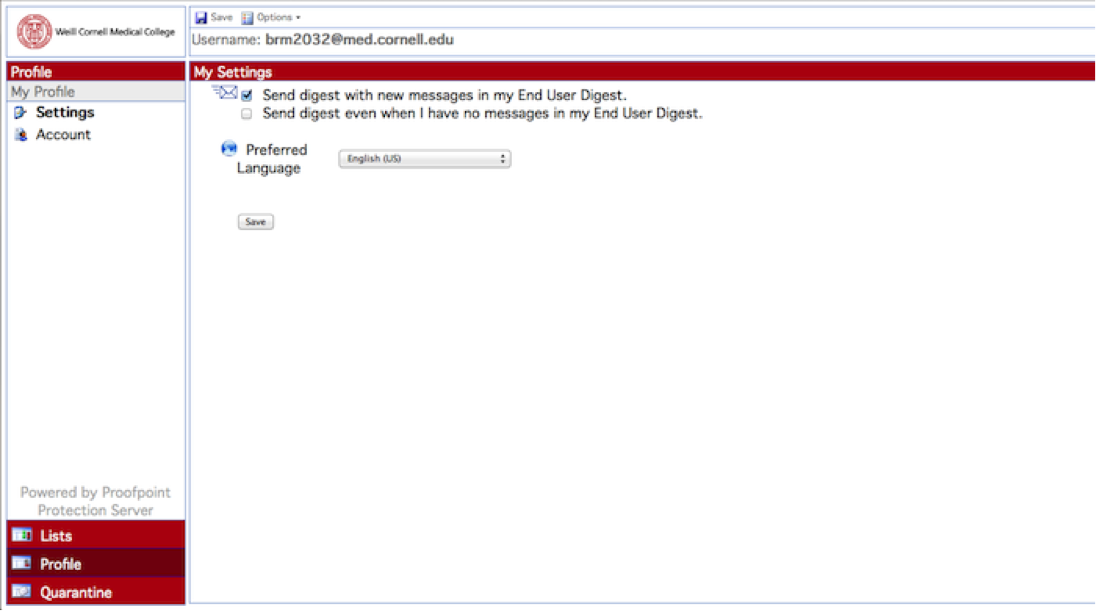
How often will I get an End User digest?
By default, you will receive an End User Digest once a day around 6 p.m. (EST) if messages have been placed into your quarantine since the last digest was sent.
I don’t want to receive End User digests anymore. How do I stop them?
If you don't want to receive a digest, you can change your settings in your Proofpoint account:
1 Log into antispam.med.cornell.edu
2 Click "Profile" on the left sidebar
3 Select "Settings"
In the "My Settings" window, uncheck the box next to "Send digest with new message in my End User Digest." If this box is unchecked, you will no longer receive a digest.
What is the Learning Management System (LMS)?
LMS is an online portal that allows WCM students and staff to conveniently review course offerings, register and complete training. Users with administrator/instructor roles can add course content and use LMS to administer training to end users.
What courses are available in LMS?
You can view available courses by logging into the Weill Business Gateway (WBG) and clicking the "My Workspace" tab, and then the "Learning" tile. You will see your own learning portal with courses you can take.
How do I register for courses?
There are three ways to register for courses depending on the course you need to take. One is to self-register. This can be done by logging into WBG and clicking the ESS tab (please review our login instructions). You can browse all course catalogs or search for a specific course.
The second way to register is for a supervisor or Department Administrator to register on your behalf. This may occur if your department determines you need access to specific applications, such as Purchasing in WBG. If this happens, you will receive notifications about how to attend training.
The third way is for a trainer/instructor to pre-register you for a course. Again, you will receive notifications from WTMS via email if this occurs.
I would like to create course content in LMS for others to use. How can I do that?
If you would like to become a Learner Administrator, please contact its-training@med.cornell.edu for more information.
I want to register for a course, but have been denied access. Why?
Not all courses are open to everyone. This is because certain courses require authorization from a Department Administrator.
One example is training for Purchasing in Weill Business Gateway (WBG). A Department Administrator determines who in his/her office will have access to this tool and registers staff accordingly.
If you feel you should have access to a course on WTMS, you can speak with your Department Administrator, or contact the ITS Service Desk for assistance.
Where can I go for support on using LMS?
Documentation on our LMS can be found on Helpfiles. For further assistance, please contact our Service Desk.
Which institutions use eduroam?
eduroam is available at hundreds of educational institutions in the U.S. and thousands more around the globe. To find out which institutions use eduroam, please click the links below:
• U.S. eduroam locations
• International eduroam locations
What is eduroam?
eduroam (education roaming) is an authenticated wireless network which allows users from participating institutions to access the Internet from any eduroam-enabled institution.
Who can use eduroam?
While on the WCMC campus:
At this time, if you work for or attend Weill Cornell, you will not need to use the eduroam wireless network while on campus. You should be using the WMC Secure wireless network to have seamless access to all WCMC resources.
If you are a WCMC visitor, you can log into eduroam provided you are part of a partner institution.
While off campus:
If you work for or attend Weill Cornell and are visiting a partner institution that uses eduroam, you can use your WCMC credentials to log into their eduroam wireless network.
What will I be able to access when logged in to eduroam at Weill Cornell?
• Access to a secure wireless network dedicated to eduroam participants
• Unrestricted Internet access which allows use of email and VPN clients
• Managed access with your home institution username and password
Does eduroam require a usage fee?
eduroam is free at all partner institutions worldwide. The providers of eduroam hotspots make the service available to benefit all members of the research and education community.
Is eduroam safe to use?
eduroam uses the security and authentication standards of each institution, so you will be accessing wireless service that typically exceeds commercial hotspots. Be aware that when using the general Internet at an eduroam hotspot, the local site security measures at that hotspot will apply to you as well. For example, the firewall settings at the visited place may be different from those you are used to at home, and as a guest you may have access to fewer services on the Internet than you have at home.
Does eduroam work on different platforms?
eduroam works on Windows, Linux, and Mac operating systems.
How do I log in to eduroam?
Connecting to the eduroam wireless is just like connecting to any wireless network on your device. You will use your WCM email address and password to connect if Weill Cornell is your home institution.
Where can I find support on using eduroam?
If Weill Cornell is your home institution, you can contact the ITS Service Desk.
If you are from a partner institution, you should contact your home institution's IT help desk.
How can I receive faxes sent to me?
Delivery options for faxes sent to your fax account (if enabled) can be configured for:
How can I send faxes?
What is device encryption, and what does it do?
Encryption is a technology that protects the contents of your device from unauthorized access by converting it into unreadable code that cannot be deciphered easily. It is a much stronger level of protection than typical security features, such as logging into an operating system with your CWID and password or protecting individual files with passwords. Whole disk encryption is used to protect the entire contents of your device.
Can I opt out of encrypting my laptop?
Encryption is a relatively easy way to safely secure the data on your laptop from theft, misuse and loss. In the event that an exception to encryption is proposed, you must complete the Request for Device Encryption Exemption form and have the request approved by your Department Administrator, the Department Chair, or an equivalent senior manager. All exemption requests will be reviewed by ITS Security. Any exemption denials may be appealed by the requestor and will be brought to and reviewed by the Information Security and Privacy Advisory Committee (ISPAC). Exemptions are granted temporarily and will need to be recertified annually and/or if the purpose of the device or the job responsibilities of the requestor change. If an exempted device is misplaced, lost, or stolen, all associated costs for forensic investigation and legal and regulatory reporting will be charged to your department. Please contact Tom Horton, Chief Information Security Officer, at thh4011@med.cornell.edu with questions on this process.
Do I have to encrypt my device?
All devices tagged by ITS and used for WCMC purposes must be encrypted using an ITS-managed encryption solution unless otherwise exempted as defined in the ITS Device Encryption policy (11.06). This is to help protect you if you store, send, or receive any of the following types of confidential data, such as:
Many people receive and store this information on their devices, even if they do not realize it, which is why we are mandating encryption on all tagged devices across the institution. The full definition of confidential data can be found in the ITS Data Classification Policy (11.03) and the ITS Device Encryption policy (11.06).
How much does it cost to encrypt my laptop?
For any ITS-tagged laptop, encryption is provided at no additional charge. We are available to assist and provide "best effort" support to encrypt untagged devices that meet our hardware requirements. Users are strongly encouraged to make an encrypted backup of the device data and verify it for accuracy and completeness.
What type of encryption software does ITS use?
ITS uses Microsoft's BitLocker Drive Encryption for devices running Windows 7 or above and Apple's FileVault 2 for devices running Macintosh OS X 10.7 Lion or above. Both of these encryption solutions are native to the respective operating system and offer significant improvement in system performance. Symantec's Pretty Good Privacy (PGP) is being phased out and may only be used to support legacy devices requiring encryption. Mobile devices, such as tablets and smartphones, are encrypted using native device encryption that is enforced by our mobile device management solution.
What can I do if my device does not meet hardware requirements?
ITS recommends Macintosh users upgrade to OS X 10.7 Lion or higher. Encryption solutions for previous versions of OS X, such as the original version of FileVault, do not provide whole disk encryption and are not compliant with the Device Encryption policy. We also recommend that Windows users upgrade to Windows 7 or higher.
I have a desktop computer that stores confidential data as defined in the data classification policy. Can I have it encrypted?
The latest revision to the ITS Device Encryption policy (11.06) now requires that all tagged desktops are encrypted with the ITS-managed encryption solution.
Do BitLocker, FileVault 2, and PGP encrypt my entire hard drive?
Yes! Many types of encryption software do not encrypt the entire drive, but the ITS-managed encryption solutions utilize whole disk encryption, which means every sector of your hard drive will be encrypted.
How long does it take to encrypt my hard drive?
It takes about 15 minutes to install the encryption software, and then between 4 and 10 hours to finish the encryption, during which time you can use your computer normally. After the initial encryption is complete, the encryption should not disturb you while you work.
Will my computer act differently after it has been encrypted?
Devices encrypted with BitLocker Drive Encryption and FileVault 2 will not require any additional steps to access your data. Both encryption solutions are native to Windows and OS X, respectively, and require no additional logins. Legacy devices encrypted with PGP will require an additional password when first powering on your device. This separate password ensures only you can access your encrypted data. You can assign a separate password for this purpose but it can be the same as the CWID password you normally use to log into your computer.
Will my computer run slower once it is encrypted?
Occasionally, there is a minute reduction in computer speed after encryption. In general, this is unnoticeable on all but very old devices, such as those more than four years old.
Should I back up my computer before it is encrypted?
Yes! While we do not anticipate having any problems during the encryption process, it is always a good practice to back up your data to an encrypted removable storage device and verify it for accuracy before encrypting your laptop. If you need assistance with your backup, please contact Support.
I store confidential data on a removable storage device (USB thumb drive, external hard drive, etc.). Can I encrypt my removable storage device using BitLocker or FileVault 2?
Yes, but due to compatibility with different types and versions of operating systems, we recommend choosing removable storage devices that are pre-encrypted that are compatible with nearly any computer. ITS is available to assist in choosing a compatible pre-encrypted drive.
Can I encrypt the device myself?
Yes, but due to compatibility with different types and versions of operating systems, we recommend choosing removable storage devices that are pre-encrypted that are compatible with nearly any computer. ITS is available to assist in choosing a compatible pre-encrypted drive.
What happens if I forget my password? Will I be locked out of my data forever?
No. By utilizing an ITS-managed encryption solution, the recovery keys are securely stored in a central system. If you need to recover your data on devices encrypted with BitLocker or FileVault 2, you will need to contact the Service Desk to validate your identity. A technician will then enter the recovery key to allow you to decrypt and access your data.
If you forget your password on a legacy PGP-encrypted device, you will need to contact the Service Desk and validate your identity. Once your identity is confirmed, the Service Desk will issue you a temporary (usable only once) password and then help you change it to something only you know.
Why and how do you verify my identity if I forget my password?
We verify your identity because we want to ensure you are who you say you are before we give you a password or enter a recovery key to provide access to your data. We do not want someone who has stolen your laptop to circumvent our encryption system by claiming to be you. Prior to encrypting your device, you will be required to sign up for the myPassword management system. You will be asked to answer 5 questions about yourself (i.e., what is your favorite color?, what city were you born in?, etc.). If you forget your password or need a recovery key, the Service Desk will ask you for the answers to some of these questions. Once you have answered them successfully, we will work with you to recover your data as described above. If you cannot remember the answers to your questions, we will require that you visit us and show an ID or, if that is not possible, fax a copy of your ID to us for verification.
How does encryption work?
There are many types of encryption but the basic concept is to encode information (data) so that only those with the right "key" can decode and use it. Keys can be any random string of letters and numbers. For more information about the various encryption solutions used by ITS, visit the links below:
I've already encrypted my device on my own. Do I have to use the ITS-managed encryption solution?
Yes. In order to properly secure and protect the information stored on your tagged device, an ITS-managed encryption solution must be used.
What is the Information Security Breach and Notification Act? What does encryption have to do with it?
The Information Security Breach and Notification Act, or ISBANA, is a New York State regulation that requires institutions such as WCMC that believe social security numbers, bank information numbers, or credit card numbers were stolen or lost from computers they own or operate (such as laptops, mobile devices, or desktops) to publically report the theft or loss to every individual affected. This is an expensive and timely process that could adversely affect the reputation of WCMC.
WCMC is requiring encryption in order to implement extra security safeguards in the event of theft or loss. Lost or stolen encrypted devices are not subject to the notification requirement of the ISBANA regulations.
How does Secure Remote Archive work?
Secure Remote Archive works through a combination of a web client and a small server software running on the user's computer. This allows unattended background transfer of very large number of files of any size.
The transfer occurs between endpoints, which are basically storage places. Typically, one endpoint would be the Remote Archive, which is located in Ithaca, and the other endpoint would be your computer.
How do I use Secure Remote Archive?
Secure Remote Archive works by transferring your files to the Cornell Storage in Ithaca.
What do I need to use the Secure Remote Archive?
To use the Secure Remote Archive, you need the following:
Note that your Globus.org account is separate from your CWID and your Cornell account. If you forget your Globus.org password, you need to contact Globus for assistance.
Who is listed in the WCM Directory?
The directory contains information about the following types of active people:
Can I remove my contact information from the WCMC Directory?
In accordance with our Directory Policy, all WCMC employees must publish current contact information in the directory. This includes:
Phone numbers
All WCMC employees must have one phone number listed published to WCMC/NYP (preferably the employee’s direct number, otherwise a department number). All exempt employees and faculty must have one phone number published publicly, meaning it is searchable on the Internet (preferably the employee’s direct number, other a department number). This number need not be published publicly for non-FLSA exempt employees.
Email addresses
All WCMC employees must have an email address published publicly. Only email addresses at the following domains are permitted to be published publicly or to the institution:
Personal email addresses or other professional email addresses not ending in one of the above domains can be set to "Emergency" in order to receive important alerts from the college.
Locations
All WCMC employees must have a location published publicly. Valid locations are available from the directory drop-down menu.
Who can see my information in the WCMC Directory?
Some information in the directory is required to be public, meaning all users, even those outside of WCMC, can see it (see more information on this). You will notice "Publish to" dropdown menus next to certain fields requesting your contact information. These dropdown boxes control settings of who is able to see your information. These definitions apply to the options for publishing various data:
Where does the data in the WCMC Directory come from?
The directory is fed from a variety of sources including:
Is the data in the WCMC Directory shared with other applications?
Data in the directory is or will be used by a variety of applications, including VIVO and Office 365. For example, Office 365 uses your preferred name and title for your college email account. Generally speaking, the following types of data are shared with other applications:
Can I include a photo of myself in the WCMC Directory?
Yes. All WCMC employees are encouraged to publish a professional business headshot to the directory. This can be done by logging into the system with your WCMC credentials, and then uploading your headshot to your profile (photographs must be a minimum of 200 pixels wide and 72 DPI in resolution).
Published photographs will synchronize with Microsoft Outlook, Microsoft Lync, and other downstream systems that use directory data.
All directory photos should meet these requirements:

Example of an acceptable directory headshot
The following types of photographs are subject to removal if uploaded to the directory:
WCMC employees may have a professional photograph taken in Art & Photography by contacting Patricia Kuharic at pkuharic@med.cornell.edu.
How do I fix incorrect information in my WCMC Directory profile?
There are some fields you can update yourself, including phone numbers and locations.
Other fields, like title, department, and email address, are verified by other departments, like Human Resources.
To change your legal name
Please complete and submit a Personal Data Change Form to Human Resources-IMS .
To change your title, department, or administrator/manager
Please contact your Department Administrator, who may submit an Employee Change Form to Human Resources-IMS .
Can I download search results from the WCMC Directory?
Yes. Users who log into the directory may download search results in a spreadsheet format. For example, let's say you want a list of current Department Chairs at WCMC. Search for "Chair," and your search will return a list of current Department Chairs. Click on the "Download..." button and select the format you would like to download the information.
How does the WCM Directory integrate with the Emergency Notification System?
The Emergency Notification System (Everbridge) is used by WCM to alert our community during emergencies. The directory links to the Emergency Notification System and supplies the contact information used.
Be sure to enter all of your emergency contact information, including where you can be reached during off-hours (home telephone, cell phone). You can select "Emergency Only" in the "Publish To" dropdown menu if you do not want the contact information displayed to others in the directory. More information on the Emergency Notification System at WCM is available at https://emergency.weill.cornell.edu/UpdateWCA.
Can I use data in the WCMC Directory to create an advanced report?
Yes. Please contact the Identity Management Team at idm@med.cornell.edu for assistance.
How do I log into a phone?
By default, your extension should be appearing on your own phone’s login screen. However, if you see a message stating "Enter Extension and press Enter or OK," use your 5-digit extension as your username and password to log in.
Can I log into another person's phone?
Yes. All Avaya phones allow you to log into another user's phone, which is a feature known as Guest Login. This is particularly useful if you have rotating staff using the same desk phone. To log into another phone, push the Home button, select Guest Login on the screen, and use your 5-digit extension and password to log in. By default, Guest Login will expire after 10 hours.
How do I retrieve voicemail when I am away from my desk?
When you miss a call and receive a voicemail, your new phone will automatically deliver the voicemail to your WCMC email account. The email will include an attached .wav audio file of the voicemail message. Additionally, you can call 646-962-6800 from any phone and use your 5-digit extension and password to retrieve your voicemail.
How do I set up my voicemail to go to my WCM email account?
To set up your voicemail messages so they are delivered to your phone, visit myvoicemail.weill.cornell.edu, log in with your 5-digit extension and password, and check your settings. You can also place a ticket with the Service Desk.
How do I bypass someone else’s voicemail greeting when trying to leave them a message?
Simply press ** when you hear the voicemail greeting.
How can I log back into my phone if another user is still logged in?
If you are at your own desk and see someone else’s extension still on your phone, push the Home button and scroll down on the screen to Log Out. Your extension should reappear on screen.
What kind of headsets can I use with my Avaya desk phone?
The new Avaya phones support most enterprise class headsets that come with a physical base. Note that you cannot use a Bluetooth headset with these phones unless it comes with a physical base.
ITS recommends the following headsets for the Avaya desk phone:
Wireless headsets:
Wired headsets:
How do I update my email preferences in WRG?
To update your email preferences:
What if my entity is not listed in WRG?
If the entity you are trying to select is not in the dropdown list, email Sponsor-Creation@med.cornell.edu with the subject "COI Entity Request" They will add the sponsor on the backend and notify you when you can go back in to select that entity.
What do I do if I'm having trouble finishing my transaction in WRG?
In many cases, the Completed checkbox must be checked before clicking Submit. If this doesn’t work, there may be required fields that are not filled out. Review the form your submitting and check for any errors or missed fields.
If you continue to experience issues, contact the Service Desk.
How do I know if my submission in WRG was successfully received?
You will receive an email confirmation. You will also receive a notification if any action needs to be taken on your submission.
I see I have an Open Action Item. How do I view more details?
If a submission is returned to you, you will see an Open Action Item on first page after login. Click the folder icon to view that action item.
![]()
What if I’m the Principal Investigator on a project for which I’m submitting a Study Specific Report (SSR)?
Select your own name from the dropdown menu.
The Exit button doesn’t work. How do I log out of WRG?
You can log out of WRG by closing your browser window.
What is Two-Factor Authentication?
Two-Factor Authentication is a security best practice that requires more than one type of security method when logging in to an application. An authentication method can include something you know (a password or PIN), or something you have (a unique code).
Two-Factor Authentication adds an extra layer of protection that makes it more difficult for anyone to gain access to your accounts, even if your password has been compromised.
How will my login experience change with Duo?
Your login experience will only change when you are accessing a Duo protected service in a way that it determines two-factor should be invoked, such as accessing myApps from another country.
You will continue to log into the service using a CWID and password, “something you know.” Duo then, based on a policy decision, asks for the second level of authentication by utilizing a code “something you have.” The code can be easily be accessed from a smartphone app, SMS, or voice call.
How do I enroll in Duo?
On your start date at Weill Cornell Medicine, you will receive an email from Duo with enrollment instructions. Click the link to continue and complete the enrollment. For a full overview of how to enroll in Duo see this KB article: Duo Enrollment Workflow.
You can utilize Duo on many devices, including:
Does the Apple Watch support Duo?
Yes, Duo supports the use of the Apple Watch to authenticate a user's session and generate a token. More information is available on the Duo website.
Can Duo be used with a physical token?
Yes. The preferred method to use Duo is by using a smartphone. However, if you do not have a smartphone, you can ask your Department Administrator to request one for you
What passwords can and cannot be stored in LastPass?
Any business account that you use in the workplace should be stored in your Enterprise account. We recommend that you do not store any personal information in the Enterprise account, but rather in a separate, personal LastPass account. If you ever have any questions, ask your Enterprise administrator. If you do choose to store any other passwords in your LastPass account they must adhere to any policies laid out by your Administrator.
Can I use LastPass on my mobile device?
Yes, with the Premium and Enterprise versions of LastPass you can install the LastPass app on your mobile devices to help manage mobile logins. LastPass supports every major smartphone and tablet, including Android, iOS, and Windows Mobile devices. More information is available here.
Does WCMC see the data in my personal LastPass account?
No, if you use a separate LastPass account for personal passwords, and even if that account is “linked” to your WCMC LastPass account for more convenient access, WCMC does not have any visibility into the contents of that account or your use of that account.
What happens if I forget my LastPass master password?
If you go to log in and cannot remember your Master Password, click on this link to enter your email and have your password hint sent to you. The information that LastPass will email you is only what you entered as your password hint when you registered your Master Password. Neither LastPass nor your company has access to your Master Password and therefore cannot send you more than your password hint, so you may need to initiate the Account Recovery process.
How do I import existing passwords (a.k.a. data) to LastPass?
For details on how to import existing data into LastPass, please see the LastPass FAQ page.
Can I use LastPass on my mobile device?
Yes, with the Premium and Enterprise versions of LastPass you can install the LastPass app on your mobile devices to help manage mobile logins. LastPass supports every major smartphone and tablet, including Android, iOS, BlackBerry, and Windows Mobile devices. More information about using LastPass on mobile devices can be found here.
How do I transfer a call to someone's voicemail without ringing their phone?
During a call, perform the following steps:
How do I change my phone's password if I use the hot-desk feature and log in at other locations?
To change your password, pick up the receiver and:
What kind of computer should I use at WCM?
ITS recommends several devices that are compatible with our security standards and applications used at WCM. For more information, please visit our Hardware Purchasing page, as well our Operating Systems page to ensure you are compliant with our standards.
Who is eligible to receive the desktop version of EndNote?
All WCM faculty, staff, and students are eligible to receive a free copy of EndNote’s desktop version, but only on an ITS-tagged device. Our licensing allows you to install a copy of EndNote on up to two devices, one of which can be a personal device.
You can also set up an account to access the web version of EndNote. You can create any login you would like (i.e., does not have to include your CWID).
How do I download a copy of EndNote?
Our licensing agreement with EndNote does not allow our users to install the software themselves. However, ITS can install a copy of EndNote on your tagged device, at no cost to you, at the SMARTDesk or by remotely logging into your computer.
Contact our Service Desk and ask one of our technicians for assistance in installing EndNote on your device.
How do I access the web version of EndNote?
Visit www.myendnoteweb.com and log in. If it’s your first time accessing EndNote online, you will need to create an account on the WCM network by connecting on campus or via VPN. You can create any username and password you would like.
Can I get EndNote if I work or study at WCM, but am on an NYP computer?
The desktop version of EndNote can only be installed on an ITS-tagged device. However, if you are part of WCM, you can still use the web version of EndNote by visiting www.myendnoteweb.com. Make sure you have already set up an EndNote account on our network before using the web version.
What is the difference between EndNote’s web and desktop versions?
Both versions enable you to search, save, and organize your references. The desktop version has more features than the web version, which are listed on EndNote’s website.
Is there a limit to the number of references I can have in my EndNote account?
If you are using the web version only, you can have up to 50,000 references stored in your account. The desktop version allows for unlimited reference storage.
If I leave to another institution, do my EndNote References stay with me?
Yes, if your new institution offers EndNote.
Can I connect my personal email account to my WCM Outlook account?
Office 365 Outlook (formerly Outlook Web Access) allows you to simplify your inbox and connect up to five additional email accounts so you can send and read all your email in one place. While this feature would permit you to connect your personal email with your Weill Cornell Medicine email account, ITS does not permit this integration.
Unlike adding separate mail accounts in the Outlook desktop client, connecting email accounts in Outlook on the web downloads and stores all external email messages in your Weill Cornell Medicine account. By virtue of this integration, all personal email will be discoverable and scanned by our data loss prevention software under the same terms as work email, as defined in the ITS 11.08 - Use of Email and ITS 11.09 – Data Loss Prevention policies. In addition, ITS will have no means of separating integrated personal email from work email. Should your relationship with Weill Cornell Medicine end, we will not be able to provide an export of your personal email messages.
For these reasons, ITS does not permit the connection of personal email accounts in Outlook on the web. If you have any questions, please contact Brian J. Tschinkel, Information Security Officer, at brt2008@med.cornell.edu.
Is SharePoint HIPAA compliant?
Yes.
Can I share my SharePoint documents with people outside of Weill Cornell Medicine/NYP?
Yes. Users from approved institutions can be granted access to files and sites in SharePoint.
How are SharePoint sites typically set up?
Our SharePoint team recommends one SharePoint site per department. This site can be broken down further into specific teams or groups, allowing certain people in your department to have access to necessary files.
Note that every SharePoint site is customized to your specifications. When you request a SharePoint site, you will meet with a developer who will assist you with creating your site and addressing your department’s specific needs.
What are the recommended uses for SharePoint?
There are multiple ways you can customize your SharePoint site, but these are a few of the features you can have:
Can I access SharePoint from home or off campus?
Yes, you can use a VPN client or access WebVPN (webvpn.med.cornell.edu). If you do not use VPN, you may need to log in with Duo MFA.
Can I edit documents within SharePoint?
Yes. SharePoint is ideal for version control to allow multiple users to edit a document and save the latest version online.
You can edit documents in a Microsoft application (e.g., Word, Excel, etc.) or within your browser.
Can I connect my team calendar in SharePoint to my Outlook calendar?
Yes. If you would like to keep track of important dates and events listed in your SharePoint calendar, you can import them into your personal Outlook account.
Instructions are available here.
How much storage is available?
Each SharePoint site comes with 5 GB of space for documents. If you require more, that can be configured into your site for an additional fee. Our SharePoint developers will confirm this with you during your initial consultation.
Which bibliographic styles does EndNote support?
EndNote currently supports over 6,000 output styles, making it easy for you to set up your bibliography the way you want it. Many styles are preloaded in the desktop client. A full list of styles is available on the EndNote website, which is also available for download to your desktop client.
How do I obtain a WCM alumni email account?
If you are a student about to graduate from a degree-granting program, you will receive an email from the Alumni Affairs office with information about registering for an alumni account. Follow the instructions provided. You may also attempt to self-provision your alumni email account by going to https://identity.weill.cornell.edu/alumni.
ITS has plans to expand this service to alums that have already graduated from Weill Cornell Medicine. More information will be available in the near future.
Will my alumni email account appear in the WCM Directory?
No, not unless you personally add it to your account.
What happens to my student email account once I graduate?
Upon graduating, you will have 90 days to register for an alumni email account and save any emails from your student account. During this grace period, please inform your contacts of your new alumni email address. After 90 days, your student account will be closed and all of your emails will be lost.
What happens to my student WCM email account if I continue to work at the institution after graduation?
All graduates, whether they stay with WCM or transition to a position elsewhere, will receive a notification to set up a permanent alumni account. If you maintain an active affiliation with WCM, your @med.cornell.edu address will remain intact, and you can also use your alumni account.
What happens to my WCM email if I transition to NewYork-Presbyterian?
A WCM email account can coexist with an NYP account for the same person. Therefore, a graduating student moving to NYP will continue to have the full 60 day grace period to save important information.
How much storage is available in my alumni email account?
Alumni email accounts hold 50GB worth of data. You can view how much storage is left in your account by clicking on the gear icon in the upper right of your account, then clicking General > My Account.
Do I log into my alumni mailbox with my CWID and password?
No. While your CWID is still the same, your user name to login is your CWID@alumni.weill.cornell.edu. Your password will be separate from your existing WCM CWID account password.
I’m a WCM student. Is there a way for me to access Adobe Creative Cloud?
Please fill out this online form to request an institutional license. Students, as well as other faculty and staff, may use Creative Cloud on public computers in the library. If you would like a personal copy of Creative Cloud, you can purchase it at a discounted rate. Visit weillcornell.onthehub.com to purchase a monthly or yearly subscription to the service with significant savings (you can compare pricing on the Adobe website).
How do I request access to a department file share
To request access to a file share, authorized users can simply log onto myHelpdesk.med.cornell.edu, and click “Submit a Request.” Your request goes straight to the appropriate ITS group for fulfillment.
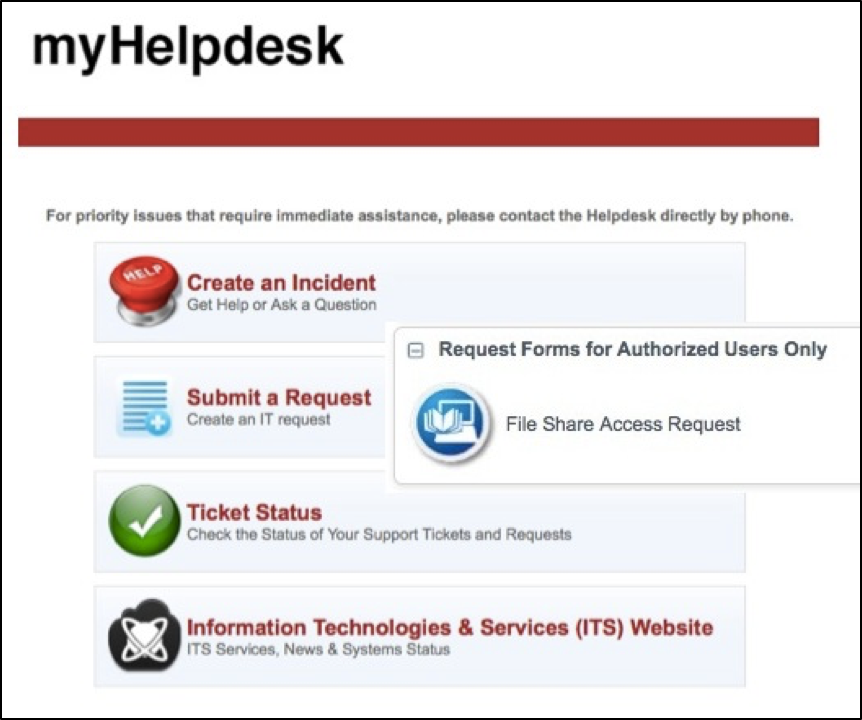
*Please note: Only owners and administrators of a file share are authorized to submit a Request through myHelpdesk. If you need access to a file share, get in touch with your Department Administrator to verify who can submit a Request on your behalf.
How do we learn how to fill out a File Share Access Request?
If you need additional support please contact ITS Training at its-training@med.cornell.edu.
Why is ITS requiring two-factor authentication?
Phishing is a leading method used by hackers to gain access to your password, data, and compromise your accounts. A second layer of security helps significantly to mitigate this risk. In fact, two-factor authentication is one of the best ways to protect against remote attacks on WCM accounts such as phishing, credential exploitation and other attempts to takeover your accounts. When two-factor authentication is enabled with web-based applications, such as myApps, remote attackers are unable to access your accounts without possessing your physical device needed to complete the second factor.
Does the phone on which I’d like to install Duo need to be tagged by ITS?
No, you can install Duo on any device whether it is tagged by ITS or not.
Do I need to be connected to the Internet to use the Duo app?
No. After you register with Duo, using the app does not require Internet connectivity. If your phone is not connected to the internet and you need to use the Duo app, choose the “Enter a passcode” option as an authentication method as shown on the screen below. This screen should appear when you try to login to a site that requires two-factor authentication.
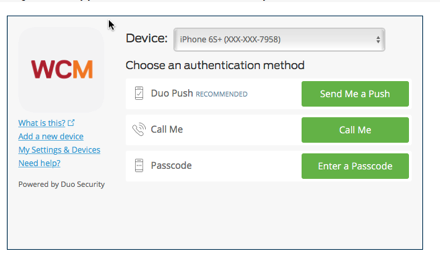
Then, get your passcode by tapping the key button on your Duo app screen. This works anywhere, even in places where you don’t have an internet connection or can’t get cell service.

If I travel abroad and buy a local phone/SIM card while I’m there, can I still use Duo to access the network?
Yes. To do this, you can borrow a FOB Key (a small authentication device) from ITS. Please stop by the SMARTDesk at 1300 York in the Library a few days prior to your departure to borrow a Duo FOB. If you travel frequently you may want to purchase your own key ($18 to $50). We suggest either the FIDO U2F Security Key, YubiKey 4 or YubiKey 4 Nano. http://www.amazon.com/s/field-keywords=yubikey .
If you travel abroad and use your own phone, use the “Enter a Passcode” authentication method to access Duo enabled sites.
Do I need to re-register my email account when I install Duo?
No.
How do I reset my voicemail password if I forgot it?
If you've forgotten your voicemail password, please send an email to support@med.cornell.edu with the following information:
Our technicians will help you reset your account to create a new password.
I am purchasing a standard computer with institution funds but it will be used strictly off-campus. What should I do?
Please contact csg@med.cornell.edu for assistance.
I want to buy one of the standard Dell bundles but need more memory or a bigger hard drive. What should I do?
Customers can now customize Dell bundles directly in the SciQuest Dell Punch-out site. You do not need to request a quote from our Procurement team. The pre-configured bundles are set with options that allow for faster shipping. While things like hard drive and memory can be upgraded, there will be an additional cost and will require 2-3 weeks to configure.
How do I purchase a workstation?
Visit the SciQuest Punch-Out site in the Weill Business Gateway and select from our various options. No quote is needed from our Procurement team to make a purchase.
How do I know if I device I want to purchase is considered standard?
Please visit our Standard Computer Specs page for more information.
What if I want to purchase an HP or other computer?
If you purchased a standard HP desktop, laptop, or workstation prior to October 25, 2016, you will continue to be billed at the ITS standard rate. However, after this date, all new HP computers connected to our network will be billed at the higher non-standard rate.
Can I purchase an ITS standard computer model through a different vendor, such as CDW-G or Best Buy?
While a model similar to one of our standards can be purchased from a different vendor, ITS cannot guarantee it will work with our approved operating system and applications. For Windows systems, ITS works closely with our vendors and system manufacturers to select the configuration that will work best with our IT services. The system will be billed at the higher non-standard rate, will require additional time to setup, and additional ITS consultation fees will be incurred to connect the computer to the WCM network.
For Apple systems, ITS has arrangements with Apple to give us the best pricing possible.
I’m getting a much cheaper price for a computer from another vendor. Should I buy it?
No, ITS strongly recommends against this. Many cheaper computers available on the market are intended for home use and generally do not meet our minimum requirements. ITS standard bundles are enterprise computers certified for extended use, which meet or exceed our minimum requirements, and are easier to service and maintain. If you still decide you want to purchase, please note the computer will be billed at the non-standard rate, will incur higher tag/connect fees, and will incur additional consultation fees for set up. Additionally, if the unit does not have a TPM chip, additional approval will be required from our ITS security team to allow the unit to be connected to the network. These devices are also not eligible for two-day connect.
Are computers that are out of warranty still supported?
ITS standard bundles come with a 3-year warranty, including HP systems purchased prior to October 25, 2016. Costs for defective parts are generally covered by the system manufacturer during this period. While systems may be used past the warranty period, ITS recommends against this. Most defective parts are generally not covered and repairs may be at more cost to you. Additional ITS consultation fees may also apply.
What does “ship within 8 days” mean?
All vendors require WCM to provide a legal document referred to as a purchase order before they release any goods. Purchase orders are issued to the vendor once an order is fully approved in the Weill Business Gateway (WBG). Once the approved purchase order is received by Dell, the computer will be configured and shipped out within 8 days.
Which ITS-supported vendors should I order computer equipment from?
Dell and Apple products (except iPhones) should be purchased through the SciQuest Punch-Out site in the Weill Business Gateway. Other hardware (e.g. printers, scanners, adapters etc.) can be purchased through CDW-G via quote by emailing csg@med.cornell.edu.
Should I get extended coverage for my desktop, laptop, workstation, or tablet purchases?
ITS highly recommends extended warranty coverage for electronic equipment. While Apple hardware does not currently come with Apple care, it should be purchased. The ITS-approved Dell bundles in SciQuest already include extended warranty coverage for three years.
Can I use the cloud storage feature from Creative Cloud?
No, Adobe Cloud storage is not available for storing WCM data.
Who do I contact for shipment status on the product I ordered if I don’t get any updates from the vendor directly?
Please contact csg@med.cornell.edu and our Procurement team will contact the vendor for shipping/tracking information.
Who do I need to contact if I need to return the product I ordered?
Please contact csg@med.cornell.edu so our Procurement team can contact the vendor for a Return Merchandize Authorization (RMA). The RMA takes a few days and will be sent to our Procurement Specialist, who will forward it to you with the electronic return label.
Please note that no exchanges are allowed with our vendors. A new purchase order will be required if another product order is needed. The fund account will be credited once the vendor receives the returned item.
Am I allowed to exchange products if the order is incorrect, unsatisfactory, or defective?
No exchanges are allowed with our vendors, but you can return the product. A new purchase order is required for the new product. The vendor will send a credit memo, so your fund number account is credited accordingly through our Accounts Payable department. Please contact csg@med.cornell.edu and our Procurement Specialist will contact the vendor for a Return Merchandise Authorization (RMA).
Who do I contact if I don’t know what specs to get for my computer?
The standard devices recommended by ITS should meet most needs. However, if you are uncertain, please contact csg@med.cornell.edu and a Procurement Specialist will provide recommendations based on your work-related needs.
What comes with my desktop? Do I get a keyboard, mouse, and monitor?
The desktops comes with a keyboard and mouse, but a monitor would need to be purchased separately. You can view our monitor options on our Standard Computer Specs page
Does WCM-ITS have a standard for monitors?
Out standard size is a 24” Dell Ultrasharp monitor. If you require a different size monitor, please contact csg@med.cornell.edu and a Procurement Specialist will provide recommendations based on your work-related needs.
Can I download Microsoft Office for Macs?
Yes, Officecan be downloaded on an ITS-tagged machine via the WCM App Store:
Is Zoom AI Companion HIPAA compliant?
Yes, WCM has a Business Associates Agreement (BAA) with Zoom requiring that any data shared in the application is protected via encryption. Users concerned with data privacy can still opt to leave the AI Companion feature off if they are hosting the meeting, or request the host to turn off the AI Companion feature if they are a meeting participant.
Will Zoom AI Companion turn on automatically once the meeting begins?
No, hosts must manually turn on Zoom AI Companion for every meeting by clicking the star icon in the tool bar:

Zoom AI Companion does not automatically collect and/or analyze data from meetings unless the host activates it, and even then, the data is just limited to the meeting audio.
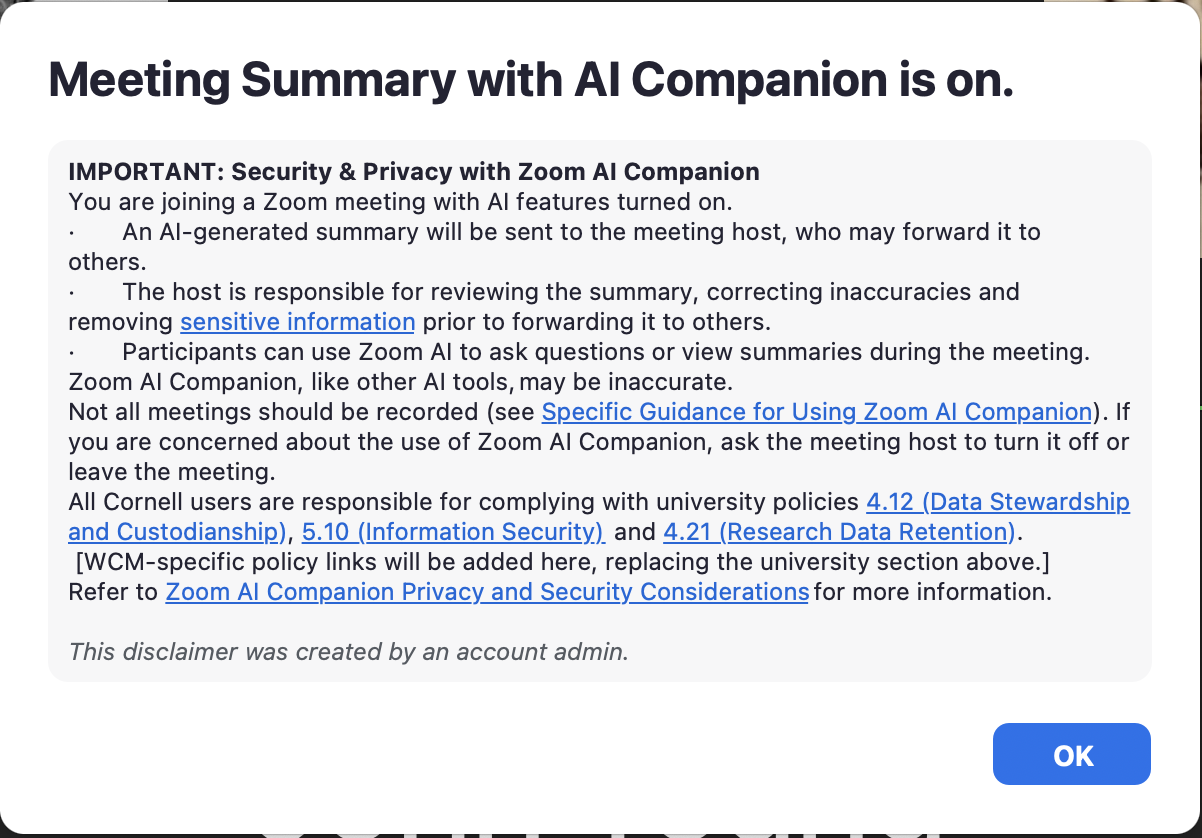
How will I know I am in a meeting where the Zoom AI Companion is turned on?
Once the host initially turns on the AI Companion, all attendees will see the following pop-up notification that the meeting is being transcribed for AI Companion:
You will also see a glowing star icon ![]() in the top right of your Zoom window any time the AI Companion feature has been activated.
in the top right of your Zoom window any time the AI Companion feature has been activated.
What if I am a meeting participant and I do not want the AI Companion feature to be turned on?
Participants can request that the host turn off the AI Companion by clicking the glowing star icon ![]() at the top right of their Zoom window and selecting “Ask host to stop AI Companion features.”
at the top right of their Zoom window and selecting “Ask host to stop AI Companion features.”
Please note that while a participant can request that the host turn off the AI Companion, it is ultimately the host's decision. If a host decides to keep the AI Companion on after a participant has requested it be deactivated, the participant can still leave the meeting.
Are there any limitations to the questions I can ask in the AI Companion window?
By default, Zoom AI Companion can only provide meeting data from the moment a participant enters a meeting. For example, if you ask for the AI Companion to catch you up on any information you may have missed, it can only provide you details from the moment you entered the meeting, and not any details discussed before you logged in.
Ideal uses for this feature may be if you’re in a meeting, but had to step away for a few moments, or to query the AI Companion about any action items you may need to complete when the meeting is over.
Who receives the Zoom AI Companion meeting summary notes and transcript once the meeting has ended?
The meeting summary and transcript will only be sent to one person – the host. This summary and transcript will be sent via email directly to the meeting host and will not be stored in the host’s Zoom account. If the summary and/or transcript needs to be shared with other participants, it is the responsibility of the host to review, edit, and distribute them, as needed.
Who receives the Zoom AI Meeting Summary if the host changes?
Only the original host (i.e., the person who created the meeting) will receive the meeting summary, regardless of whether they transferred host rights to another participant.
What meeting content does Zoom AI Companion process and summarize?
Zoom AI Companion at WCM is configured to only process the meeting’s audio. Meeting chats and shared content (e.g., slides shown on screen) are not processed and will not be included in the summary notes once the meeting has ended.
Does Zoom store any data to transcribe meetings?
Zoom holds data for 30 days in case of support needs. The company does not use any customer audio, video, chat, screen sharing, attachments, or other communications-like customer content (such as poll results, whiteboard, and reactions) to train Zoom’s or its third-party artificial intelligence models. You can review Zoom's privacy and security policies for more information.
Can I use a third-party AI plugin in my Zoom account?
No, third-party plugins have not been reviewed to ensure they meet security standards to protect data shared in Zoom. If you have a specific use case and would like to speak with ITS, please contact our Service Desk.
How do I request the creation of a WCM email/calendar account?
As of January 23, 2017, a specific subset of WCM faculty, staff, and students will get Office 365 email/calendar accounts created automatically when their CWID is created.
Office365 email/calendar accounts will be automatically created for:
All others should ask their departmental or divisional administrator to activate the account via the Identity Dashboard.
How do I access Box?
Go to box.weill.cornell.edu, or wcm.box.com, and input your CWID and password.
What is the file size limit when uploading to Box?
There is a 15GB file size limit.
Can I use Box to store sensitive data that is covered by laws such as HIPAA and ePHI?
Box should NOT be used to collect, process, store or share ePHI, FERPA, PII or sensitive restricted data until further notice. This service should never be used to store high-risk data, as outlined in our Data Classification policy:
Which web browsers does Box support?
Box supports the latest versions of Internet Explorer and Safari, the latest release version of Chrome, and the latest version of Firefox. For more information and to view the list of officially supported browsers by Box.com please visit the Box website.
Where can I go for additional Box help?
More info is available at success.box.com and on Box’s support site. Help is also available from the ITS Service Desk.
What are the benefits of Box over other popular commercial services, like Dropbox?
Dropbox and Box share some of the same functionality. However, Box is designed for enterprise-level solutions for large organizations while Dropbox is geared toward consumer use.
Box offers features like content and task management, online workspace for collaboration, user and group permissions, admin account transfers, and a built-in editor. In addition, Box can be used securely over the WCM network, using your institutional credentials to log in.
How do I download Box Sync?
Box Sync allows you to mirror data stored on Box to your desktop. You can then navigate and modify content stored on the Box website through your computer's native file browsing interface, without using a web browser. Content that syncs down to your computer are available for offline access.
To install Box Sync, you must be on a managed device. For Windows users, this means that when you log into your machine and go into your Start Menu, you will see a program called Software Center to install ITS-approved applications (read download instructions for Software Center). Managed Mac devices all have an ITS tag number and an application installed called Self Service. Self Service permits you to download Mac versions of ITS-approved software (read download instructions for Self Service).
Please note that if you attempt to download Box Sync from the Box website, it will not work on ITS-managed devices.
What service can I use to store PHI?
Departmental file shares, OneDrive, and SharePoint are appropriate for storing PHI.
Can I synchronize Box data on any device?
Box Sync, the application used to synchronize your Box files locally to your computer or mobile device, can only be installed on a tagged and managed device. This restriction is in place to ensure Box data is not permanently stored on unknown or unmanaged WCM devices.
How can I access my Box data from an untagged device?
You can access your Box data from any internet-connected device by going to the Box website at box.weill.cornell.edu.
Why use the web and desktop version of Box Notes?
The good thing about the desktop app is that you can create and edit Box Notes any time instead of logging into Box and searching for a note you may have already started. Notes you create in the desktop app sync to your account automatically. Plus, the desktop app keeps your notes in one place instead of trying to remember which folder you placed a particular note. Note that you cannot include high-risk data, like HIPAA or PHI info, within your Box Notes (see Section I of our Data Classification policy).
Can I use the Box Notes desktop application offline?
No, you must be connected to the Internet in order to use the desktop application. This allows your notes written in the desktop version to sync to your Box web account, so you can access your content from either application.
What if I need to host a Zoom meeting for more than 300 people?
If you need to host a larger meeting or webinar, please see this myHelpdesk article for instructions.
Why can’t I log into Zoom?
Log into your WCM Zoom account at weillcornell.zoom.us with your CWID and password. If you are having issues logging into Zoom please email support@med.cornell.edu.
Is Zoom HIPAA compliant?
Yes, Zoom signs the HIPAA Business Associate Agreement (BAA) for healthcare customers like WCM, meaning that Zoom is responsible for keeping patient information secure and reporting security breaches involving personal healthcare information. Zoom protects and encrypts all audio, video, and screen sharing data. You can use Zoom’s screen sharing, and video and audio conferencing to meet with patients and other healthcare professionals.
Even with these security measures in place, ITS strongly advises that you do not share PHI or PII-related information via screen sharing, recording, and file sharing to protect confidential data at the college. Read more information on Zoom and HIPAA compliance.
To ensure that your Zoom meeting meets HIPAA security standards:
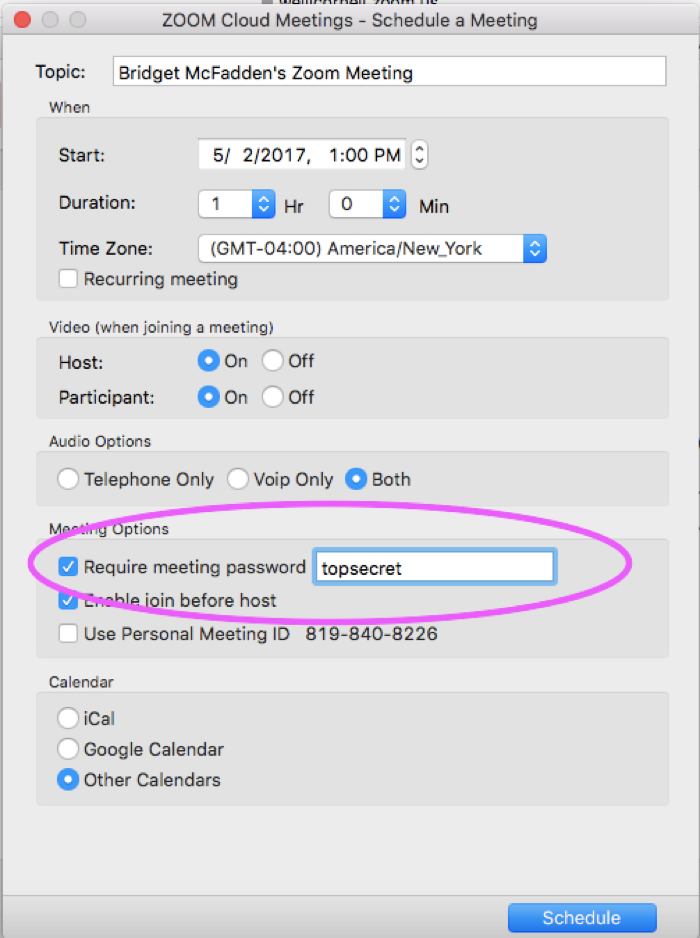
Can I schedule and start a Zoom meeting from from Outlook?
Yes. First you need to install the Zoom Microsoft Outlook Plugin. The Zoom Microsoft Outlook Plugin is designed to make scheduling a meeting in Microsoft Outlook quick and convenient. The Plugin allows you to schedule and start instant Zoom meetings, as well as make existing meeting events Zoom meetings. The Outlook Plugin will also sync free/busy times to the Zoom Client based on your Outlook Calendar events (requires version 3.5 or higher - download the latest version).
For more on how to schedule a Zoom meeting from Outlook go here How to Use the Microsoft Outlook Plugin.
Can I schedule a recurring Zoom meeting?
Yes. When you open the Zoom Scheduler in your Zoom account, you can select various different settings for your meeting. To schedule a recurring meeting, check the box next to “Recurring Meeting” in the Zoom Scheduler. The meeting ID will be the same for all instances of the recurring meeting. For more information on how to schedule a meeting go here How to Schedule Meetings.
Is there a limit to the number of people I can have in my Zoom meeting?
Yes. You can have 50 people in a regular Zoom meeting.
How do I share my screen during a Zoom meeting?
Zoom allows for screen sharing on desktop, tablet and mobile devices running Zoom.
Here are step-by-step instructions on How to Share Your Screen During a Zoom Meeting.
How do I share a PowerPoint presentation during my Zoom meeting?
Dual Screen: If you are screensharing with PowerPoint and have a dual screen or secondary projector, please click Swap Displays to switch the presentation screen during Slide Show Mode.
Slide Show in Full Screen and Chat: If you are showing a presentation in Full Screen and you want to use the Chat feature in Zoom, please change the Set Up Show to Window mode.
More information here: https://support.zoom.us/hc/en-us/articles/203395347-Screen-Sharing-with-Powerpoint]
How do I join a Zoom meeting from a PC or Mac?
There are several different ways to join a Zoom meeting from your Mac or PC, including by email link, web browser or Zoom app. Here are step-by-step instructions on How to Join a Zoom Meeting.
How do I join a Zoom meeting from mobile device?
Here are step-by-step instructions on How to Join a Zoom meeting from Android or iOS.
I scheduled my Zoom meeting for one hour. Will it end automatically when the hour is up?
No, the meeting will not end until the host ends the meeting.
Can I schedule a meeting and make someone else the host?
Yes. To pass “Host” permission to another participant select “Manage Participants” from the Zoom meeting window. Then, select More next to the participant you'd like to make host and select "Make Host."
How do I host or join a scheduled Zoom meeting?
If you are the HOST and you need to start a meeting, you have a few options:
If you are a participant and you need to join a meeting, you have a couple options:
For more details read How Do I Start or Join a Scheduled Meeting?
How do I provide a reusable meeting link for all the Zoom meetings I host?
Your Personal Link/Personal Meeting ID can serve as a reusable link for any Zoom meeting you host. You can use this to start an instant meeting or schedule a meeting in the future. To view and/or modify your Personal Link or Personal Meeting ID:
What is a Personal Meeting ID and Personal Link?
You can use your Personal Meeting ID and/or Personal Link it to start meetings at any time or schedule meetings for future use.
To learn how to customize your PMI and Personal Link click here.
Can I upload files to a Zoom meeting?
No.
What is the difference between WebEx and Zoom?
This article published by IT@Cornell summarizes the difference between these two video conferencing tools. WebEx will be phased out at WCM in June 2017. Read What it the difference between WebEx and Zoom?
How do I record a Zoom meeting?
Recording for WCM Zoom is local only. References in the vendor documentation to cloud recording does not apply.
https://support.zoom.us/hc/en-us/articles/201362473-Local-Recording
How do I use a Zoom whiteboard?
The Zoom whiteboard feature will allow you to share a whiteboard that you can annotate on with others. https://support.zoom.us/hc/en-us/articles/205677665-How-Do-I-Use-Whitebo...
How do I share my screen during a Zoom meeting?
Zoom allows for screen sharing on desktop, tablet and mobile devices running Zoom.
https://support.zoom.us/hc/en-us/articles/201362153-How-Do-I-Share-My-Sc...
How do I share a file during a Zoom meeting?
In-Meeting file transfer allows you to send files to other meeting participants once in a meeting.
Note: This feature will not work in Zoom Webinars and will not work if End-to-End encryption is turned on.
https://support.zoom.us/hc/en-us/articles/209605493-In-Meeting-File-Tran...
Can I join two Zoom meetings at once?
You can be in more than one Zoom meeting simultaneously, but not on the same device. For example, you could join one Zoom meeting on your desktop, and another from a phone or tablet.
I am a hiring manager/administrator who received an error message when I clicked on the Recruiting Management tile in My Workspace. What should I do?
If you receive the error message below, it means you have no job requisitions available:
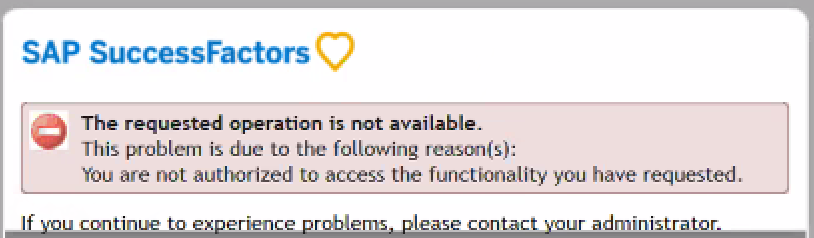
However, if you are expecting to see a job requisition and you continue to see the error, please contact the HR Solution Center at hrsc.med.cornell.edu or 646-962-9247.
Why can’t I see the My Workspace tab when I log into the Weill Business Gateway?
By default, the My Workspace tab is the third tab you should see when you log into the Weill Business Gateway (WBG). However, if you had previously customized your tab order, My Workspace will appear at the very end of your tabs. Depending on how many tabs you have access to, My Workspace could be pushed off the screen. You can reset your tabs or move the My Workspace tab to your preferred location to see it.
To reset your tab order, click the Personalize link above all of your tabs, and select Reset Order of Tabs:

To move your tabs around, hover your cursor over the top-left corner of any tab until a shaded triangle appears, and then click and drag it to the location you prefer.
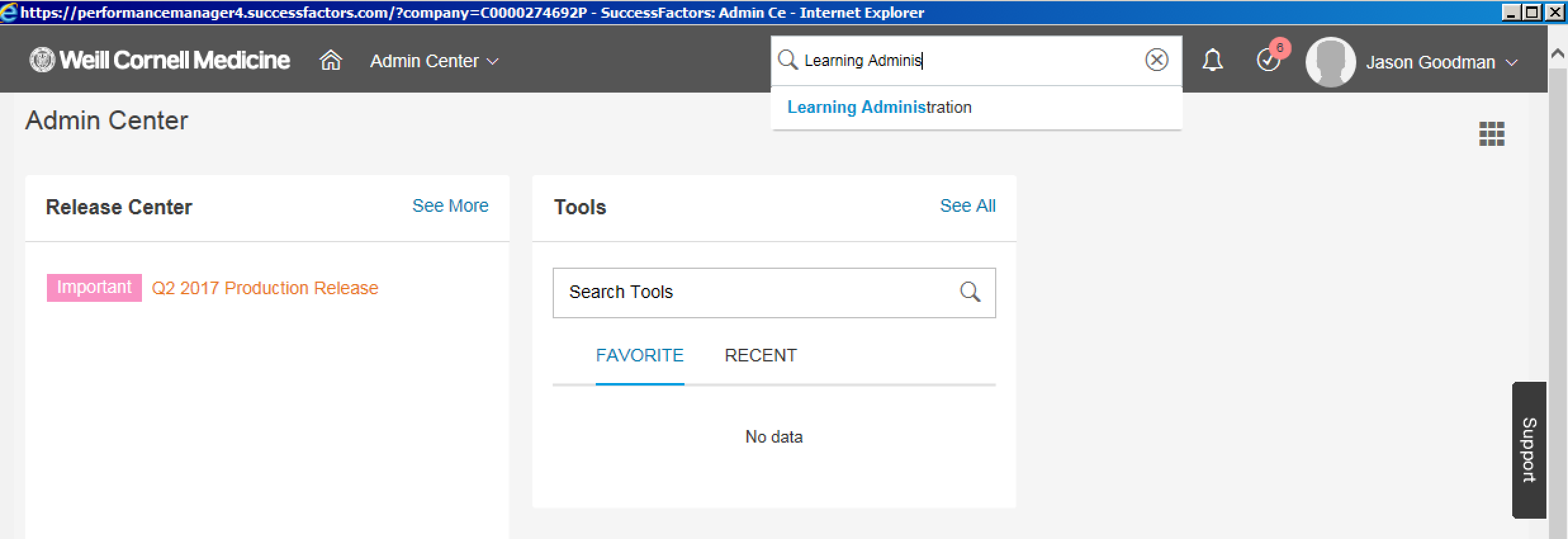
I am a Learning Administrator. Why can’t I access the Learning Administration dashboard in the LMS?
If you are a Learning Administrator and you cannot access the Learning Administration dashboard, please confirm that you have logged into the Weill Business Gateway using myApps. This dashboard is only visible via myApps. To access the Learning Administration portal via myApps:
Why do I see a pop-up blocker error message when I click on a tile in My Workspace?
You may receive the following error if you are in the Weill Business Gateway (WBG) while using Internet Explorer 11:
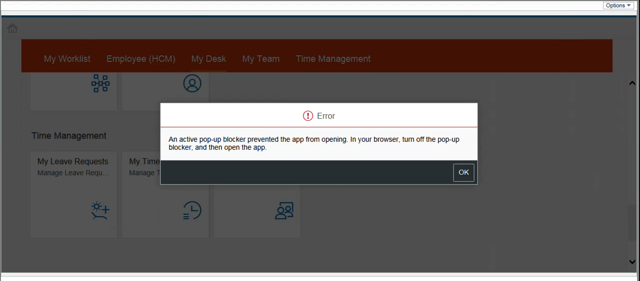
This may appear if you click on the following tiles: Learning, Careers, My Dashboard, Recruitment, or Admin Center. To avoid this issue, please sign into WBG via myApps by going to myapps.weill.cornell.edu, signing in with your CWID and password, clicking the WBG icon, and then launching the My Workspace tab.
I have a CWID and password. Why can’t I access Learning (LMS), My Dashboard, or Careers?
You are most likely receiving an error when attempting to access Learning, My Dashboard, or Careers, because the system does not yet have a profile for you.
If you are a new WCM employee, in most cases, access should be provisioned within one to two days of completing your onboarding paperwork with Human Resources.
If you are a new WCM non-employee, in most cases, you will receive a system-generated email informing you that you have been assigned training in the Learning system. In other cases, your WCM sponsor or contact may inform you that your access has been set up, with instructions on how to log on to take training.
For more assistance, please contact the ITS Service Desk at support@med.cornell.edu or 212-746-4878 with the following information:
How can I map my departmental file share to my computer?
Please follow these instructions to manually map a departmental file share to your Windows or Mac computer.
I have a CWID and password. Why can’t I access Weill Research Gateway (WRG)?
You are most likely receiving an error when attempting to access Weill Research Gateway because the system does not yet have a profile for you.
If you are a new WCM employee, in most cases, access should be provisioned within one to two days of completing your onboarding paperwork with Human Resources.
If you are a WCM non-employee and require access to WRG modules, please contact WRG Support at wrg-support@med.cornell.edu or 212-746-4878 (menu option 2, then option 1), with the following information:
Can I use Box to collaborate with colleagues at Cornell University?
Weill Cornell Medicine Box users can collaborate with faculty, students, and staff at Cornell's Ithaca campus by logging in to Box through the WCM authentication system in their browser before accepting a Box invitation. To access Box, WCM users can go to box.weill.cornell.edu and input their CWID and password. Learn more at WCM Box Cloud Storage.
It's recommended that WCM Box users authenticate through the WCM system. If accessing Box through CUWebLogin at cornell.box.com, WCM users should select "Not a part of Cornell University," enter their WCM email address and password, then authenticate to the WCM system.
Can I use OneDrive to store and share HIPAA or PHI-related content?
OneDrive is the preferred method for storing WCM high-risk data (i.e. PHI, PII) in the cloud.
Currently, you can use OneDrive to share high-risk data only with Weill Cornell Medicine faculty, staff, and students. We are working rapidly to enable external data sharing and collaboration with affiliate institutions, including NYP.
Can I use Teams to chat with anyone at WCM?
Yes, if your contact has an @med.cornell.edu email address, they will be available on Teams. Please note that this does not include WCM-Qatar or Cornell Ithaca.
Can I use Teams to chat with people outside WCM, like NYP staff?
Outside users from certain peer institutions (like NYP, MSK, and the Ithaca campus) can be added as guests to Teams by submitting a request. Guests have limited access to Teams functions, which is detailed in this Microsoft Guide. We are exploring solutions to cross-connect our chat systems with NYP and will have more information in the future.
Can I share high-risk data (like HIPAA-protected patient data) through Teams?
Yes! For most regular use cases, especially with other WCM faculty/staff/students, Teams can be used for collaboration on high-risk data.
Is Teams replacing Zoom?
There are currently no plans to replace Zoom. We still recommend that you use Zoom for pre-scheduled meetings, especially with attendees who are outside of WCM. Teams has collaboration features that let you quickly turn a one-off chat into a screenshare or video call.
We use Skype for Business all the time. Is it going away?
Yes, Skype for Business will be phased out in Spring 2020. We recommend you move to Teams soon to simplify your transition in the spring.
Can I share files on OneDrive with people outside of WCM?
ITS has an approved list of affiliates you can share data with on OneDrive. You can share files with anyone using these domains in their email address:
Please note that all .edu domains are approved by default.
On which devices can I use OneDrive, or install the OneDrive sync client?
How much data can I store in my WCM OneDrive account?
Can I request to share files with an external party or institution that is not on the approved list?
Can I store Protected Health Information (PHI) in my LabArchives account?
PHI can be stored in LabArchives. Notebook owners and administrators are responsible for ensuring that PHI within a notebook is not shared with anyone except for individuals explicitly authorized according to the IRB and Data Use Agreements. This applies both to sending of exported notebook material, and to providing shared access to a notebook or notebook pages.
How can I tell if I'm being recorded on Zoom?
When attending a Zoom meeting, the host has the ability to record meetings and can manage recording access for other participants in attendance.
To confirm if a meeting is being recorded, look for the red circle in the top-left side of your Zoom window with the word Recording:
Information on how to record and manage recording settings is available on myHelpdesk.
Note that while you can see that a meeting is being recorded, Zoom does not provide any indication when a participant takes screenshots of the meeting window. Please exercise caution and do not display any sensitive data.
Can I store Intellectual Property in my LabArchives account?
Intellectual Property can be stored in LabArchives with appropriate user precautions to protect data as in any other tool. For more information, contact ctl-connect@cornell.edu.
Will LastPass or ITS know the passwords stored in my LastPass accounts?
No. LastPass employs a "zero-knowledge" security model. This means that all sensitive data is encrypted locally at the user's device with a key that is never shared with LastPass or ITS. This model was put to the test during a network breach in June 2015. While master usernames and other data were breached, the encrypted user vaults remained secured. LastPass took immediate action to lock down user accounts and to inform its base.
Is LastPass the same company as 1Password or OnePass?
No. While these companies offer similar password management services, LastPass is its own unique product and company, with its own special set of features. Visit the official LastPass FAQ page
How is LastPass different from myAccount?
myAccount is our official password management service for WCM. It is where you will go to create or change your official WCM password. However, LastPass can be used as an optional support tool to help you manage passwords for both WCM and your personal accounts. It can also help you remember longer and various passwords, if you tend to forget them. It is safer to have LastPass manage your passwords rather than write down what your passwords are somewhere else.
How does eConsent work?
A computer or touchscreen device can be used to complete eConsent. The participant’s signature will be captured digitally via the signature field.
eConsent can be used in-person, or remotely. If eConsent is used as a method of remote consent, the subject will need to provide an email address to access the eConsent tools. However, please be aware, if you do not use WCM approved tools for remote consenting, it does not qualify as eConsent and you will not be able to collect valid electronic signatures. For further information on remote consenting methods, please refer to the FDA guidance.
What eConsent options are available?
WCM currently supports two eConsent tools: REDCap and DocuSign.
How can I use eConsent?
Both REDCap and DocuSign are available to WCM/NYP researchers. Currently for FDA-regulated studies, which require 21 CFR Part 11 compliance, only DocuSign can be used. For studies that are not FDA-regulated, REDCap can be used.
What approvals are needed to use eConsent?
All use of eConsent must be IRB approved before it can be implemented. Downloadable template language that can be used in the IRB application is available within the JCTO Researcher's Toolbox, titled "Remote Consent IRB Submission Language" under the Regulatory Tools and Templates section. Study teams must also have an IRB stamped ICF.
Does eConsent support ICFs in multiple languages?
Please email econsent-support@med.cornell.edu for additional information.
What special considerations should be given to the use of eConsent for pediatric studies?
Please email econsent-support@med.cornell.edu for questions regarding use of eConsent for pediatric studies.
Are there fees associated with eConsent?
REDCap eConsent is a free service provided by the CTSC. Any enhanced services (e.g., project build-out by CTSC member) may require a fee. DocuSign eConsent is fee for service. Current fees can be found on the JCTO website. Questions regarding the cost of service or billing should be directed to: JCTOOperations@med.cornell.edu.
How do I request and build a REDCap eConsent project?
For instructions on how to create a REDCap eConsent project, please read this knowledge article HowTo: Create eConsent Form on REDCap.
Please contact econsent-support@med.cornell.edu for more information.
I have created the REDCap project. Can I begin consenting?
Once you have created the REDCap eConsent project in development status, the next step is to promote the project to production status within REDCap and email econsent-support@med.cornell.edu.
Once it has been submitted, the project will undergo review by the JCTO. The study team will be notified within one week if the eConsent project has been approved or additional changes need to be made. Consenting within REDCap cannot begin until the REDCap eConsent project has been approved.
Does REDCap eConsent support ICF amendments or changes?
REDCap eConsent supports version control of the ICF documents.
Once the IRB has approved a protocol amendment or continuing review that include changes to the ICF, these changes can be made in REDCap by the study team. Any change to the ICF requires re-review by the JCTO by emailing econsent-support@med.cornell.edu. It is the study teams’ responsibility to keep the eConsent up-to-date, including amending the project every year after the IRB issues a newly stamped ICF at the time of continuing review (even if there are no other changes). For instructions on how to amend a REDCap eConsent project, please read this knowledge article HowTo: Amend REDCap for eConsent.
Will participants get a copy of their consent?
The REDCap eConsent form can be designed to send the participant an email that includes a PDF of their signed consent form. Please email econsent-support@med.cornell.edu for guidance.
How can the study team get access to the completed consent forms?
Signed consent documents will be housed electronically in REDCap's File Repository.
Do I need to upload the eConsent into Epic and OnCore since it’s stored in REDCap?
Yes, REDCap eConsent will create a PDF of the document which you will need to download and upload into OnCore and Epic.
Can my external site collaborators use my eConsent project?
It’s strongly recommended that non-WCM sites use their own institution’s eConsent system. The regulations required for eConsent may vary per local and/or state laws, as well as institution-specific policy which WCM-supported systems may or may not be able to adhere to.
How do I request a DocuSign eConsent?
Please contact econsent-support@med.cornell.edu to request an account.
How do I login to DocuSign?
Once your account has been activated by the JCTO, login via app.docusign.com and enter your WCM/NYP email address and follow the single-sign-on process.
I have created my eConsent in DocuSign, can I begin consenting?
Yes, you can begin a soon as you have created your template. You do not need validation from the JCTO.
Does DocuSign eConsent support ICF amendments or changes?
DocuSign eConsent supports version control of the ICF documents.
Once the IRB has approved a protocol amendment or continuing review that includes changes to the ICF, the updated ICF can be uploaded into DocuSign by the study team. It is the study teams’ responsibility to keep the eConsent up-to-date, including amending the project every year after the IRB issues a newly stamped ICF (even if there are no other changes). The JCTO does not need to review any updates to the eConsent in DocuSign.
Will participants get a copy of their consent from DocuSign?
Yes. Once the ICF is completed by all parties, the participant will receive an email with a link to download the fully executed ICF. The study team should explain to participants that they should download the PDF as soon as possible, because it will only be stored in the DocuSign repository for 12 months.
How can the study team get access to the completed forms in DocuSign?
The consenting investigator will automatically have access to the completed ICF and should ensure they download it for their research records as soon as possible as it will only be stored in DocuSign for 12 months. DocuSign can be designed to send a link to other study team members as well. Please refer to the DocuSign knowledge base article for guidance.
What happens to my LastPass account if I leave WCM?
Your institutional enterprise account would be converted to a personal LastPass account if you leave WCM. Items that might have been shared with you among WCM colleagues within the enterprise account would be lost, but personal items saved in the enterprise account would remain available to you. To ensure no data loss, we recommend that personal items are stored in a personal consumer LastPass account. That personal account can then be linked to the enterprise WCM account. While you are at WCM, you can login and use your WCM account as your daily driver with all the premium features and access to the personal identities, due to the linked account setup.
You can find out more about linking your accounts together in our LastPass guide.
How do I access the Apollo wireless network?
Where can I access the Apollo wireless network?
You can access the Apollo wireless network at the following locations:
What internet resources can I access on the Apollo wireless network?
The resources available to you on Apollo are similar to what you’d get on a guest network at a coffee shop. Most internet sites will be accessible, as well as print.weill.cornell.edu, but WCM resources, like fileshare, will not. For those, you’ll need a device that can access the WCM network.
What is a softphone?
A softphone is a virtual phone that is accessed via a computer. While you are assigned a telephone number, you do not need a physical handset to make or receive calls. All calls can be made through your computer, so long as you have an internet connection and ITS-approved headset.
What happens to my CrashPlan account if I leave WCM?
Upon leaving the institution, CrashPlan users have a 30-day data retention period. We highly recommend finding another data backup solution during this period to ensure your information is protected.
How do patients consent to be contacted for research?
During Epic MyChart (also known as Connect) eCheck-In, patients are given the opportunity to indicate their preference (Yes, No, or Undecided) and sign a consent form to participate in CCR. Patient preferences are then stored in a secure database.
Who is eligible for the Consent to be Contacted for Research protocol?
Any patient with a visit at NYP-WCM (including East and Lower Manhattan campuses) and/or NYP-Columbia is eligible for the CCR protocol.
Can I see the patient’s Consent to be Contacted for Research preference in Epic/MyChart?
No, researchers will not be able to see if a patient has indicated that they are interested in being contacted for research through their chart directly and should contact ccr-support@med.cornell.edu for more information.
How can I use the Consent to be Contacted for Research protocol to recruit patients for my study?
The CCR protocol allows researchers to recruit patients who meet your study inclusion criteria and have consented to be contacted for research.
How do I get started using the Consent to be Contacted for Research protocol?
Investigators interested in using the CCR protocol as one of their research recruitment methods should email ccr-support@med.cornell.edu with a brief description of their study (incl. IRB protocol number) and patient cohort of interest. The study team will need approval from the Institutional Review Board (IRB) and Protocol Review and Monitoring Committee (PRMC) to use the CCR protocol.
The study team will then meet with the Research Informatics (RI) team to discuss the project and assess the feasibility of using CCR as one of the recruitment methods. The goals of the consult session are for the study team to better understand the overall CCR workflow and for the RI team to begin drafting a computable phenotype of the study’s inclusion/exclusion criteria. Once the study cohort has been identified, researchers will be given the list of patients in Epic whom they are able to message to via MyChart.
Are there fees associated with Consent to be Contacted for Research?
Currently, there are no fees associated with using the CCR protocol.
How do I request an Evergreen laptop?
Anyone with access to a fund number in ServiceNow can request a laptop for themselves or another user in their department by submitting the Evergreen Request Form.
Who is the owner of an Evergreen laptop?
In the Evergreen program, ITS owns the laptop, warranty, and the relationship with our vendors. Thus, when a user no longer needs their laptop it must be returned to ITS.
Should I contact ITS, Dell, Lenovo, or Apple if my device requires service?
Users should always contact ITS first since ITS owns the device and the warranty. If ITS cannot resolve the laptop’s problem and it is still under warranty we will provide you a loaner while your device is serviced. Your laptop will need to be returned to the SMARTDesk at 1300 York Ave. or, if you are remote, ITS will ship you a loaner, and instructions for sending back the faulty device. If ITS cannot resolve the laptop's problem and your device is out of warranty, you will receive a replacement.
Do I pick up my Evergreen laptop in person or can it be shipped?
Evergreen laptops can be either picked up in person at the SMARTDesk at 1300 York Ave, or shipped to a user’s home or office. A departmental FedEx number will be needed for billing if the laptop is shipped.
How do I return an Evergreen laptop?
If a laptop is no longer needed, submit the Evergreen Request Form and choose “disenroll an Evergreen device.” You can choose to either drop off the device in person or ship it back to the 1300 York SMARTDesk.
I need to assign an Evergreen laptop to a different user, what do I do?
Submit the Evergreen Request Form and choose “Transfer an Evergreen device to a new user.”
I want the same make and model computer as an Evergreen, but I want to purchase it outright and not enroll in the Evergreen program. What do I do?
You should Request a hardware quote and indicate why the Evergreen program isn’t a good option for your use case.
I have a question about my bill, who can I contact?
Questions about billing should be sent to ITS-Finance@med.cornell.edu.
Can I run a report on my department's Evergreen devices?
Your BI billing report will show laptops being charged a “device fee;” these are Evergreen laptops. You can also submit a general IT request or contact your departmental liaison if you need a specific report.
What is the turn-around time between requesting and receiving an Evergreen laptop?
If there are no delays in ITS getting inventory from our vendors, then the typical turnaround time is about 3 days from request to either shipment or pickup. Note that the chosen method of shipment (overnight, 2-day, ground) also impacts the time it takes to receive a laptop.
Can I swap out my Evergreen PC for an Evergreen Mac or vice versa?
To swap out a device, first submit an Evergreen Request to enroll a new user. Once the preferred device has been received, submit an Evergreen Request to disenroll a user on the old device.
Is there a specific headset or other accessories that work with the Evergreen laptops?
ITS recommends the Jabra Evolve 40 headset for all Evergreen laptops.
For a full list of accessories (aka peripherals) we reccomend for use with the Evergreen laptops, please view this KB Article: Evergreen Recommended Peripherals.
Does the Evergreen laptop come with a built-in camera?
Yes, all Evergreen laptops come with a built-in camera.
Does the Evergreen laptop come with any other accessories, like a laptop sleeve or keyboard?
No. You can expect to receive the laptop and power cord. All other accessories should be purchased through the purchasing portal by your department.
Should I return my laptop accessories to ITS when I return my laptop?
No. Any accessories should be returned to your department.
How do I get Adobe applications installed on my Evergreen laptop?
Can someone other than the intended user pick up the Evergreen laptop at the SMARTDesk?
ITS prefers that the intended user of the Evergreen laptop pick up their machine, or have it shipped to their home. This helps ensure a successful first time log-in experience.
Are there any fees to disenroll an Evergreen laptop?
No. Billing will stop once the disenroll request is processed.
I use a MacBook Pro and my menu bar icon is hidden behind the camera housing. What do I do?
Your MacBook Pro with Liquid Retina XDR display features a camera housing built into the screen bezel. If app controls or menu bar items appear blocked or hidden behind the camera housing, you can turn on "Scale to fit below built-in camera" for the app to adjust the active area of your display. This ensures the menu bar and app windows appear below the built-in camera on your Mac and are always visible.
If you turn on "Scale to fit below built-in camera" for an app and the app has menu bar items or windows that would appear behind the camera housing, all open apps or apps that share the same space appear below the camera until you quit the app using the scaled setting.
For full instructions view this support article from Apple: https://support.apple.com/en-us/HT212842
I'm having issues connecting to AnyConnect VPN on my Evergreen. Am I doing this right?
1. When the Cisco AnyConnect screen appears during your Evergreen PC/Mac setup, make sure "Weill Cornell Medicine VPN - User" appears in the window. If this is missing or you have problems connecting, type: "vpn.weill.cornell.edu/wcmvpnuser" in the window. Click Connect.
2. In the Username window, enter your CWID. In the first Password window, enter your WCM password.
The Second Password window is tied to Duo, and you have two options:
Option 1: Type the word "push" into the Second Password field. A Duo notification will automatically be sent to your device of choice (i.e., a mobile device, a tablet, or your landline). Verify your identity with the chosen method. Note that the Duo confirmation expires after about two minutes. If this happens, you need to log into AnyConnect again.
Option 2: Type a one-time Duo passcode into the Second Password field. (You need a mobile phone for this option.) To generate a passcode, open the Duo app on your mobile device or tablet. Select the Weill Cornell Medicine token, and tap the down arrow on the right of the screen. A six-digit passcode will display. Enter this code in the Second Password Field.
Click OK.
What do I do with my current computer when I get my new Evergreen computer?
If you are currently using an ITS-tagged computer, follow the steps below depending on the type of computer you are using.
1) If you are using an Evergreen computer, return it to ITS.
2) If you are using a personal computer, it is yours to keep. You have a few different options:
a) Your computer can remain supported (i.e. tagged) and you can continue to use it as a work computer. This requires your department to continue to pay connect fees. Contact your Department Administrator to determine whether this is an option for you.
b) Your computer can be disconnected if you no longer need it as a work computer. Contact your Department Administrator to begin the process of disconnecting.
3) If your computer is department-owned, contact your Department Administrator.
Your DA will help you determine which steps to take next. (e.g. Return the computer to the ITS department, return the computer to your department, or keep the computer as a personal device. This requires the permission of your DA, and requires you to submit a disconnect request.)
How do I find the tag number on my Mac?
For instructions on how to find the ITS tag number for your Mac computer, check out this Knowledge article: HowTo: Find the tag number for your Mac
Who is the Research Data Retention policy for?
These policies apply to the Cornell community based out of Ithaca, Weill Cornell Medicine, and Cornell Tech.
Who should read the Research Data Retention Policy?
Anyone at Cornell University, WCM, or CornellTech who are involved in the design, conduct, or reporting of research at Cornell University.
What is the purpose of the Research Data Retention policy?
What does the Cornell University Research Data Retention policy mean for WCM researchers?
Section 1.38 details the responsibilities of WCM faculty regarding collection and retention of research data and should be read carefully by WCM researchers. Your main responsibilities include:
What kind of data do I need to deposit?
Faculty must enter into the WCM Institutional Data Repository for Research (WIDRR), at minimum, the location of their datasets (including raw data), and provide a methods file sufficient for replication and audit of the research.
In addition, faculty should:
Basic and translational science
Clinical science
When does the deposit of data into WIDRR need to occur?
Data should be deposited into WIDRR upon any of these three research milestones:
What is considered close-out of research?
How long does data need to be retained?
Primary data and supporting images must be available for at least six years after publication. If data and images are used in a subsequent publication, or cited in a subsequent publication or grant application by faculty, then data must be available for an additional six years.
What do we mean by raw data?
The WCM definition of raw data for retention purposes is the following:
WCM leaves to the PI the responsibility to determine which appropriate format to use for their raw data according to the standards in their respective fields (i.e. the raw data format usually required by journals in the field).
Should I archive the raw data of a paper I authored but not as first or last author (co-author)?
If you are collaborating with researchers outside of the institution, including institutions located abroad, and this collaboration results in (a) published manuscript(s), you are responsible for archiving the raw data that pertains to your contributions in the publication(s). The same logic applies to grant applications.
Who will have access to the research data in the repository?
Cornell University and WCM: Cornell and WCM have the right to access all research data generated under their auspices, supported by their funds, or conducted using their facilities. They have the right to take custody of research data.
WCM Faculty, PI: WCM faculty, PI, or other researcher who leaves the University may request a copy of research data for projects on which they have worked. Submit requests to Senior Associate Dean of Research or Senior Associate Dean of Clinical Research.
Section 1.3.10 contains full details on Research Data Access.
What does the Research Data Retention Policy say about publication?
Section 1.3.11 contains full details on Publication.
What are Cornell and WCM's rights and responsibilities in regard to research data?
Cornell and Weill Cornell Medicine own the research data and related property rights that arise from the activities of their researchers and others who use university resources. This includes resources provided through grants, contracts, awards, or gifts.
What are the Principal Investigator’s (PI) rights and responsibilities in regard to research data?
Within the limits set by the superseding authority of Cornell, agreements with collaborators, and any applicable terms within sponsored agreement, the Principal Investigator (PI) has the right and authority to control the use of and access to any research data conducted under their management, including data used in publications or presentations. The PI is responsible for maintaining and retaining data, and ensuring their integrity. Full list of responsibilities found in section 1.3.6.
How do I access the WCM Data Retention & Export Control Attestation?
The WCM Data Retention & Export Control Attestation, a 20-minute course covering both new Cornell University policies, will be available as of July 11, 2022 in the Learning module of WBG (LMS). The Attestation records your understanding of and agreement with the research data policies.
1. Navigate to the Weill Business Gateway (wbg.weill.cornell.edu) and click the Learning tile. Or use the link: http://sf-lms.weill.cornell.edu/
2. On the My Learning homepage, there is a Find Learning search box. Type WCM Data Retention & Export Control Attestation in the search box and click Go.
For full instructions view this Knowledge Article: HowTo: Find a Course in SuccessFactors Learning Management System
If the Attestation has been assigned to you, follow these instructions: HowTo: Start a Course in the SuccessFactors Learning Management System
When do I have to take the WCM Data Retention & Export Control Attestation?
As of July 11, 2022, Faculty have 60 days to take the course and attest that they abide by its policies. The Attestation should be complete no later than September 16, 2022.
What WCM-supported data storage tools integrate with WIDRR?
The following list of data storage tools are WCM-supported and/or WCM-implemented. They comply with the new Data Retention policies, and integrate with WIDRR
How do I register my badge with Imprivata Tap and Go?
Once you receive your Tap and Go license, please follow these instructions to register your WCM ID card.
I don't have my ID card. Can I still log in with Imprivata Tap and Go?
Yes. Imprivata Tap and Go also allows staff to sign in with their CWID and password. Watch our video about logging in for more information.
How do I get access to Imprivata Tap and Go?
Imprivata is only available to clinical departments. You can request badge readers and licenses on our myHelpdesk site. If you have questions about implementing this service in your department, please contact your ITS Departmental Liaison for assistance.
Does Teams Voice have a physical phone option?
Microsoft Teams Voice does not have a physical phone option at this time. You can, however, install the Teams client on your smartphone, and use that as your physical device to make and receive calls.
I have an Avaya phone. How do I access the Avaya softphone?
Visit myHelpdesk and use our IP Phone and Call Center Services Order Guide to request access to the Avaya virtual phone application. You can do this by selecting Activate Softphone for an existing number under “Request Type.”
There is no additional cost for this service.
Do I have to keep a standard IP phone handset if I have a virtual phone?
No, you do not need a physical Avaya phone if you just want the Avaya Softphone.
This depends on your needs. If you have an Avaya handset for your office, but frequently visit other office locations or have a hybrid work schedule, you can request the Avaya virtual phone application and transfer your calls when needed to your laptop or mobile app.
However, if you are in the office infrequently or work fully remote, you can just use the Avaya Softphone or opt for Teams Voice, which does not require a physical handset at all. Calls be taken solely from your computer or smart device with the Teams mobile app.
How long will I be signed into my computer by using the badge reader?
Imprivata provides a grace period of 4 ½ hours once you initially log in. This is done to prevent someone from using your credentials maliciously. An example of your day may be:
Start of shift:
8 am: badge tap and password (extra security measure)
8 am – 12:30 pm: badge tap only to login/out
Lunch:
12:30 pm – 1 pm
Return to shift:
1 pm: badge tap and password
1 pm – 5:30 pm: badge tap only to login/out
I lost my WCM badge. How do I log into my workstation?
You can still sign in using your CWID and password to your computer. To replace your badge, contact WCM’s Security Department at 212-746-0911. You'll need to re-register your new ID card in order for it to work with your installed Tap and Go badge readers.
What happens if I forget to log out of my Tap and Go workstation?
Computers with Imprivata installed will detect idle activity and automatically lock if no one has been working at the computer for several minutes.
For shared computers, Imprivata includes a security feature called “Fade to Lock,” which gradually obscures all content on the screen after a set period of inactivity:
12 minutes of inactivity: Screen will begin to fade
6 minutes after: Warning appears with a countdown timer
18 minutes after: Workstation locks
Please note that while Imprivata provides some security measures for inactive computers, it is vital for all WCM staff to take precautions when working with sensitive data and lock workstations immediately before leaving their desks.
For more information on logging out of a Tap and Go computer:
I tried to sign into Imprivata, but see an error message that reads “Incorrect Username or Password.” What should I do?
If you’ve confirmed that you are inputting your WCM credentials correctly and you still are unable to sign in, please contact the Service Desk at 212-746-4878.
I’m trying to tap in with my badge, but don’t see the Imprivata login screen. What do I do?
In this case, it’s likely that the Imprivata app is installed, but not running, due to someone exiting the app. To open the app again, go to Windows Start > All Programs > Imprivata Agent (restart agent).
A strange icon is appearing in my Imprivata app. What does it mean?
There are a number of icons that may appear on your screen. Here's what they indicate:
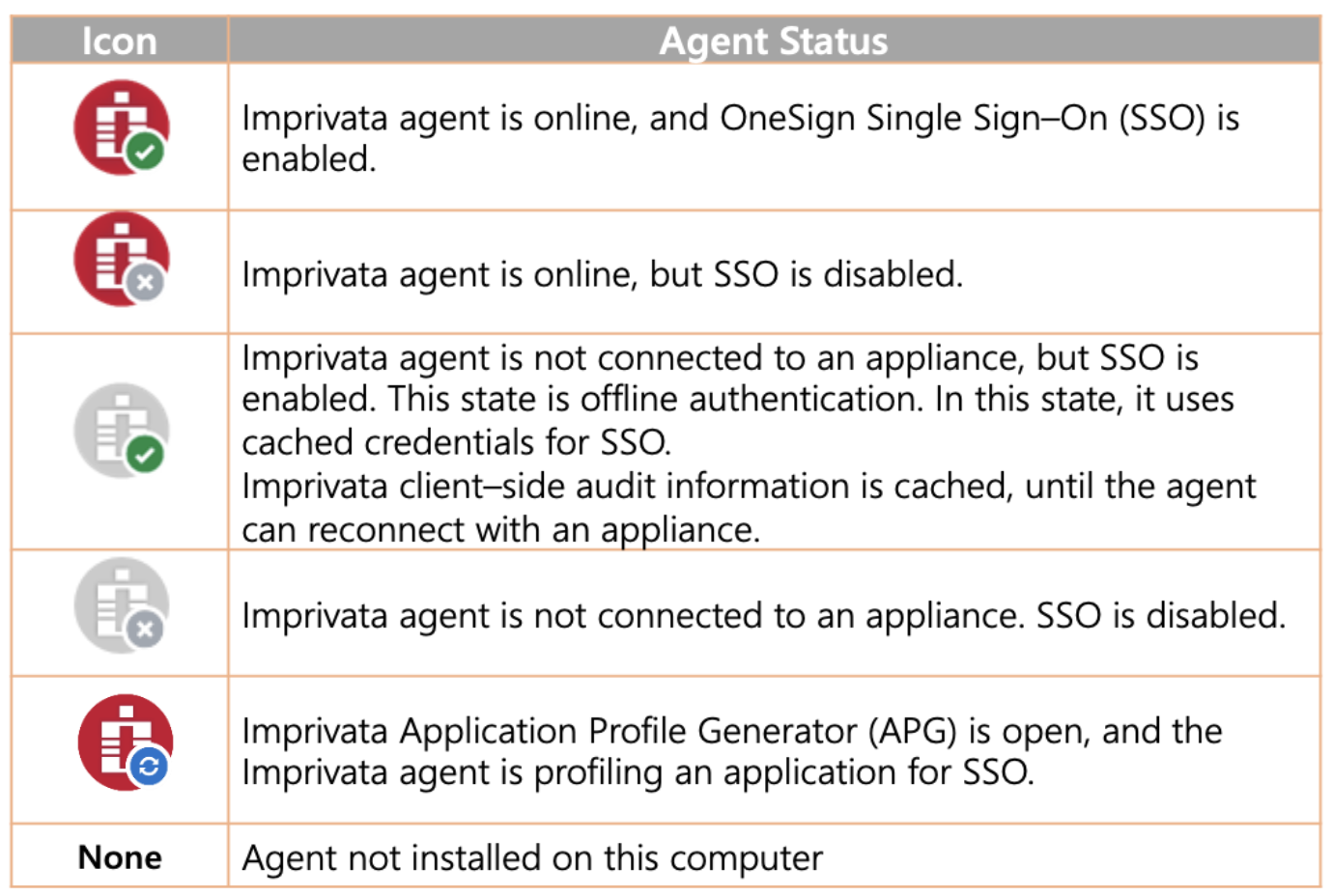
What does the Cornell University Research Data Retention policy mean for WCM researchers?
Section 1.3.8 details the responsibilities of WCM faculty regarding collection and retention of research data and should be read carefully by WCM researchers.
Your main responsibilities include:
What kind of data do I need to deposit?
Faculty must enter a data catalog record (marked public or private) into the WCM Institutional Data Repository for Research (WIDRR). That record should include the location of the datasets (including raw data) and provide the methods file sufficient for replication and audit of the research. It is not mandatory to deposit the datasets into WIDRR if it is available in an existing data repository.
In addition, faculty should:
Basic and translational science
Clinical science:
How long does data need to be retained?
Primary data and supporting images must be available for at least six years after publication. If data and images are used in subsequent publication, or cited in a subsequent publication or grant application by faculty, then data must be available for an additional six years.
What is raw data?
WCM definition of raw data for retention purposes is the following:
“Data considered as raw data are any final file generated by instruments used to collect raw data prior to any additional filtration, data cleaning, or analysis work.”
WCM leaves to the PI the responsibility to determine which appropriate format to use for their raw according to the standards in their respective fields (i.e., the raw data format usually required by journals in the field).
Please contact the library (https://library.weill.cornell.edu/ask-us) with any further questions.
Should I archive the raw data of a paper I authored but not as first or last author (co-author)?
If you are collaborating with a study team external to WCM, including institutions located abroad, and this collaboration results in publication(s), you are responsible for archiving the raw data that pertains to your contributions in the publication(s) (e.g., if your contribution was a figure, then provide the raw data & methods file for that figure). The same logic applies to grant applications.
Imprivata was installed on the computer I use, but I do not have a registered badge. How should I log in?
You have two options:
You can still log in using your CWID by typing CUMC\yourCWID in the username field, and then typing in your password.
I keep receiving an automated message to enroll my badge, despite having already done so. What does this mean?
You may have already enrolled your badge, but might still receive this message from Imprivata:
You recently enrolled a badge with Imprivata. If you believe this is an error, contact your help desk immediately.
Typically, staff tend to wear multiple badges at once on their lanyards. The best way to resolve this would be to separate the badges because if multiple cards are brought close to the reader, it cannot easily distinguish which card you want to register. If you continue to experience this issue, despite only using one badge, please contact the Service Desk.
Will my Evergreen laptop work at the hybrid workstations that are available at 575 Lex?
Yes!
My Evergreen laptop is lost or stolen, what should I do?
If any Evergreen laptop is lost or stolen, the user should contact their supervisor immediately. Then, the user or their supervisor should submit two critical forms on myHelpdesk. First, submit the LOST OR STOLEN DEVICE REPORT form as it is critical that our Privacy Office and Security Teams can carry out the proper protocols for a lost piece of IT Equipment. Then submit the EVERGREEN LAPTOP REQUEST form and choose “disenroll an Evergreen user,” so that ITS stops monthly billing for the laptop. ITS will follow up with the department and user as needed and the department can expect to be charged for the remaining value of the device.
What kind of permissions does Duo need on my phone?
What kind of data does the Duo app collect?
What kind of data does the Duo app not collect?
How do I request a new REDCap Project?
You can create a new project directly in REDCap via the + New Project tab. You will be able to access the new project immediately after answering a few short questions. Within 24 hours after creating a new project, you will receive an email from redcap@med.cornell.edu with a link to a survey asking for more detailed project information. You will have up to six weeks to complete this survey.
Are there fees associated with using REDCap?
REDCap is available free of charge for research studies, but services such as SUPER REDCap and other projects with sophisticated needs may require financial support from Investigators.
Where can I learn how to use REDCap? How I request training for REDCap?
You can register for a REDCap User Training Workshop on the home page of REDCap after you have logged in. There are training workshops for beginner and advanced users. For WCM users, you can request individual training from the REDCap Additional Services Request form.
How do I cite REDCap in my publications?
For studies that use REDCap for data collection, the publication will need to cite the Clinical and Translational Science Center (CTSC) grant. “This work was supported by grant number UL1 TR 002384 from the National Center for Advancing Translational Sciences (NCATS) of the National Institutes of Health (NIH).”
What is development mode in REDCap? What is Production mode?
All projects begin in Development status. The main difference is that in Production mode, if changes affect your data, it will need administrator approval, otherwise the system will automatically approve the change. This ensures that users do not change fields that might potentially change data analysis. If you have tested your project and are ready to collect data for your study, you should move the project to production.
How do I add new users to my REDCap project?
In the left-hand menu, under applications, select “User Rights.” You will be able to add new users with their CWID. For CTSC partners, you can request access from redcap@med.cornell.edu. On this same page, you can add, edit, or delete user roles. User roles have preset user rights for the project you are working in.
What are my options for user permissions in REDCap?
The creator of the project will modify and edit the user permissions by using the ‘User Rights’ section in the left-hand menu. User permissions can be set at the individual or group level. User roles can be created for the group level and are useful when you have several users with the same privileges. Roles categorize users within a project and can be modified to have specific privileges.
How do I log into REDCap?
For Weill Cornell Medicine associates, log into REDCap using your CWID credentials. For all others requesting access, sponsorship must be provided to receive an account, please email redcap@med.cornell.edu. If you are not logged into a WCM network or the VPN, you will need to complete the Google Authentication step, or you can send a security code to your email.
How do I reset my password in REDCap?
A. For non-WCM/NYP users: On the login screen, select ‘Forgot your password?’ This will prompt you to the REDCap Password Recovery page. If it is an authentic REDCap account, an email containing a link for resetting your password will be sent to the primary email address associated with your REDCap account, after which you will then be able to log in to your account.
B. For WCM/NYP users: Your login is authenticated using your CWID. If you need to reset your password, you will need to change your CWID password through your institution’s identity management system.
Are REDCap survey responses collected anonymously?
While REDCap is technically capable of anonymous data collection, the accurate configuration of the REDCap project will depend on your requirements and how the project was started. Please contact redcap@med.cornell.edu for a consultation about collecting anonymous responses.
What approvals are required for my REDCap research projects?
If the project utilizing REDCap involves human subjects research, it must have IRB approval before moving to production status and collecting data. If the project utilizing REDCap involves animals, it must have IACUC approval before moving to production status and collecting data.
Can REDCap connect to other sources of record?
Offered as a premium service, SUPER REDCap enables pre-population of case report forms with data from electronic health record (EHR) and research systems. SUPER REDCap provides an adjudication process whereby users can approve all incoming data from a source system, such as Epic. For further information, please contact redcap@med.cornell.edu.
Should I use the O365 or desktop version of Microsoft Visio?
Use Visio for O365 if you:
Request/keep the paid desktop version of Visio if you:
For a complete comparison, please see KB0017334.
For a detailed description on how to access Visio for Teams, please see KB0017339.
How do I access the Remote Apps portal?
Do I need to be on VPN to access Remote Apps?
No, Remote Apps is accessible from any Windows or Mac device anywhere with a browser and an internet connection.
What do I need to access Remote Apps?
Mac users need to install Microsoft Remote Desktop from the WCM App Store before accessing Remote Apps. Windows users need to use the Microsoft Remote Desktop app that is already installed on their computers.
How do I request access to an application on Remote Apps?
Anyone with access to a fund number in ServiceNow can request access on myHelpdesk by submitting Remote Apps request form. If you are not authorized to use the department fund number, please reach out to the Department Administrator to get the access.
Place a request on and specify which app you need access to:
How do I request an application to be published on Remote Apps?
Please send an email to RemoteAppsSupport@med.cornell.edu so that ITS can consult with you and understand your requirements.
Is this email from Wells Fargo legitimate?
Probably!
You receive email notifcations from Wells Fargo when you submit a Payment Requisition or Travel & Expense eForm in WBG, and choose to have your payment issued via direct deposit. These emails may have the EXTERNAL tag on them, but they are not spam.
What do you need to know about Wells Fargo notifications?
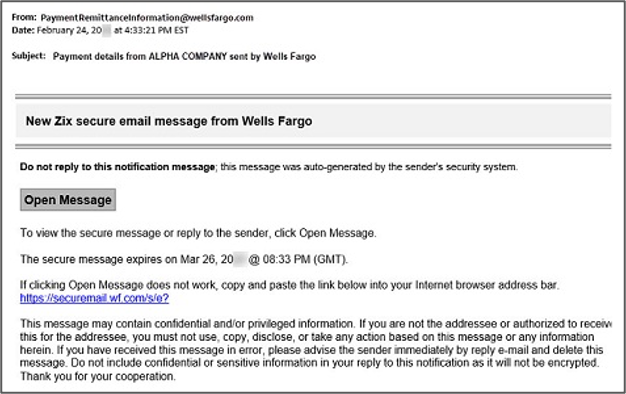
What do you need to do if you receive an email from Wells Fargo?
Questions?
Contact the Electronic Commerce Services (ECS) Delivery Team at 1-800-851-8311, option 4, Monday through Friday, 7:00 a.m. to 10:30 p.m. Eastern Time.
How do I open a co-managed AWS account?
You can submit a request for an account using our Research Computing/Storage Request form on the myHelpdesk site.
What can I use an AWS co-managed account for?
AWS accounts can be useful for several types of scenarios, including, but not limited to: developing and testing environments, running data for research or experimentation, creating hands-on training environments, innovating and prototyping proof-of-concepts, and for managing Agile and DevOps practices.
Are there any limitations on using an institutional AWS account?
Self-service cloud accounts are not intended for sensitive or confidential data. There are guidelines and access controls that are not in place to prevent unauthorized access or accidental exposure of sensitive information.
Accounts are also not suitable for hosting critical production systems or applications without proper governance and oversight. Mission-critical applications and systems may require specialized infrastructure, high availability, and more stringent operational processes that necessitate centralized management and monitoring.
For more information, please review our Cloud and AWS security standards.
Why should I open an AWS co-managed account with ITS rather than directly with Amazon?
ITS would still provide a centralized oversight function. This ensures governance, compliance, and alignment with organizational policies and standards.
What am I responsible for should I manage an AWS co-managed account?
How can I request a CWID?
Only Department Administrators/Designees and Division Administrators can make requests for CWIDs using our CWID Request Form. Please note that you must be on the WCMC network or using VPN if off-campus to view the form.
What happens if my server disk is running out of space?
The Operations team will email the system owner regarding the alert, advising them to clean up or increase the disk. If the owner does not respond after three emails, the Operations team will automatically increase disk space.
I don’t see an option for my preferred pronouns. How can I add them?
The Office of Diversity and Inclusion collects feedback on how to promote inclusivity on campus. If your pronoun is not available from the options in the dropdown menu, please use the survey link in your profile to inform the team of which pronouns you’d like to add.
Do I have to add my pronouns?
No, this is optional.
Where will my pronouns display once I’ve updated them?
For now, your pronouns will display on the Summary tab of your WCM Directory listing. They will notautomatically appear in your email signature. We are exploring ways to apply these settings to other third-party applications, and will share updates when we know more.
What is R?
R is a programming language and software environment that is widely used across many disciplines for statistical analysis, data visualization, and data science.
What is RStudio?
RStudio is an integrated development environment (IDE) specifically designed for the R programming language.
Users can install a free and open-source version of RStudio on their local laptops.
What is RShiny?
RShiny is a software package for R (and Python) that allows users to easily develop interactive web apps and dashboards for their data projects. It is useful for visualizing data dynamically and creating tools and analytics for other researchers.
What is Posit Enterprise?
Posit Enterprise offers additional features and capabilities, compared to the free and open-source version of Shiny, that enhances collaboration, security, and scalability within the WCM environment.
Posit Enterprise provides a robust and enterprise-ready platform for R-based data science workflows and applications.
The majority of WCM users use R locally through a free installation of RStudio on their local machine. Research Informatics cannot provide support for users experiencing issues installing or configuring the local, client-side RStudio application.
What functions does Posit Enterprise offer?
Posit Connect: Posit Connect is a publishing platform that enables researchers in the WCM community to share their RShiny webpages with others. It allows you to deploy Shiny applications, R Markdown documents, and other R-based and Python based assets to create interactive reports, dashboards, and data-driven applications.
Posit Package Manager: Posit Package Manager is a comprehensive package management solution. WCM researchers can create and distribute internal R packages, ensuring consistent package versions.
How can I deploy an RShiny app?
If you have an RShiny app that you would like to deploy, you can submit a Research Computing/Storage Request Form and someone from the Research Informatics group will set up some time to go over application requirements, and deployment workflow.
How do I access Posit Connect?
Visit the URL for your instance and log in with your CWID and password. Each project will have its own individual instance and the URL will differ accordingly.
Research Informatics grants access to a specific instance of Posit Connect after verifying that users have appropriate regulatory permissions.
Using Posit offsite: If you are not connected to the WCM network (i.e. offsite), you must be logged into Cisco Secure Client VPN to access Posit Connect.
Who should users contact with questions about Posit Connect?
Users can contact arch-support@med.cornell.edu with questions about Posit Connect.
Can I access Posit Connect on mobile?
Yes, but functionality will be extremely limited. We recommend that you access the system on a desktop computer.
How can I join the email list for Tech Tuesdays?
We email information on the latest session every week to our ITS-Users listserv. If you believe you’re not included in ITS-Users, please reach out to ITS Communications to be added. You can also visit the WCM Events page to register for upcoming sessions.
Are Tech Tuesday sessions recorded?
Yes, we typically record Tech Tuesday sessions. The only time we do not record sessions is when sensitive information may be used in a demonstration, but this will be announced at the beginning of the session. You can view recordings of past sessions on our Tech Tuesday playlist.
Where can I find recordings from past Tech Tuesday sessions?
Visit the ITS YouTube channel to view our Tech Tuesday playlist.
I have an idea for a Tech Tuesday topic. How can I share it with ITS?
We’d love to hear your ideas! Please submit your feedback using this form.
I’m interested in attending a Tech Tuesday session, but I have a conflict. What should I do?
Even if you can’t attend a session, we highly recommend that you register so you can receive follow-up information, like the session recording and help guide links.
Do you offer one-on-one training sessions for any of the topics covered during Tech Tuesdays?
Opportunities for one-on-one trainings vary by topic and the availability of a given facilitator to meet outside of Tech Tuesday. However, you can try reaching out to the facilitator, who is usually copied on follow-up emails, or contact the ITS Communications team, who can put you in touch with the right person.
Are there other resources I can use to learn more about ITS-supported services?
Yes! We highly recommend accessing your free LinkedIn Learning and Skillsoft accounts for on-demand courses.
Are the services mentioned in Tech Tuesdays free to access?
Yes, most applications and services featured during Tech Tuesdays are free to WCM users. One of the goals of Tech Tuesdays is to ensure we focus on services that are widely accessible to faculty, staff, and students. However, some of the applications we feature may include a nominal fee. This is always discussed during the session, and if there is a free alternative, we will also mention it. Overall, the featured services are selected based on attendee feedback and the benefits our staff feel an application would bring to the WCM community.
Why haven’t you hosted a session about [insert application name] yet?
We would love to host as many sessions covering as wide a range of applications as possible! Some reasons we may not have covered a topic yet are:
However, with technology needs changing all the time, we encourage you to submit your ideas for topics. We may be able to present it at a later date, or find a suitable alternative to demonstrate.
Can I use Consent to be Contacted for Research as my only recruitment tool?
No, consent to be contacted for research is not designed to be the sole recruitment tool. CCR can be used in addition to traditional recruitment methods.
What should I do if I cannot access the LMS?
If you are a student, fellow, NYP employee, affiliate, or temp employee, you cannot access the LMS through WBG. Instead, use this direct link: http://sf-lms.weill.cornell.edu
Enter your CWID and password in the corresponding fields and click Login. Prior to entering your CWID and password, you may be asked to select your primary institution from a list.
If you are a WCM employee and you cannot access the LMS or a course, please contact wbg-support@med.cornell.edu or call 212-746-4878, option 2 and provide the following information:
Do I need cloud expertise to use cloud services offered by ITS?
This depends on the specific cloud service. In general:
What are the cost differences between cloud service models?
Who manages the infrastructure and support of ITS' cloud service options?
Can I use PHI/PII data in any of our cloud service models?
Yes, all SSOD and Managed cloud accounts support PHI/PII data and comply with NIST 800-53 rev 5 and AWS Guardrails. However, Co-Managed solutions must be reviewed on a case-by-case basis for supported data types.
What are some example use cases for each cloud service model?
How do I get started with Copilot Chat?
Is my data secure when using Copilot Chat?
Can I use Copilot Chat to interact with other Microsoft services?
Can I use Copilot Chat on multiple devices?
What languages does Copilot Chat support?
Can I customize the responses from Copilot Chat?
What is the difference between Microsoft Copilot Chat and the full version that integrates with work data?
Microsoft Copilot Chat is an AI-powered assistant that helps with various tasks and queries. It uses the OpenAI ChatGPT engine but does not train the model. It can be accessed on desktop (Windows and Mac) and mobile devices (iOS and Android). The key features include instant assistance, boosting productivity, accessing information from various devices, collaborating efficiently, and enhancing user experience through natural language processing.
The full version that integrates with work data, Microsoft 365 Copilot, offers additional capabilities by leveraging the Microsoft Graph API. This integration allows for deeper interaction with other Microsoft services and applications, providing more comprehensive data analysis, advanced collaboration features, and enhanced automation capabilities. The full version is designed for more complex and integrated use cases within the Microsoft ecosystem
What information is available in the Tripartite Directory mobile app?
The app includes profiles for faculty, staff, and medical students from WCM, NYP, and CUIMC. Additional user groups, such as non-medical students, will be considered for future enhancements based on organizational needs.
How do I search for a colleague in the Tripartite Directory app?
Use the search bar at the top of the app to enter a name or CWID. The search function is designed for flexibility and allows full or partial names (first, last, or both).
Please note that employees may be listed under their preferred name or their formal/legal name, which might differ from the name they are commonly known by. If a name search doesn’t return expected results, try alternate name variations. For the most accurate results, use the CWID as it is a unique identifier.
Does the NIH Public Access Policy apply to all Research Informatics services?
The services provided by the Architecture for Research Computing in Health (ARCH) program are supported by the WCM CTSC. Please contact arch-support@med.cornell.edu for further information.
How can I learn more about the NIH Public Access Policy?
In addition to visiting the NIH policy page, the WCM Library has a recorded presentation and a LibGuide.
How can I get more information about how to cite the WCM CTSC grant?
Additional information can be found on the CTSC Citing Support page.
What’s the difference between PrinterLogic and PaperCut?
PaperCut is a printing service used exclusively by WCM students.
What do I do if a printer is not appearing in the PrinterLogic app?
There are three common reasons why a printer may not be appearing in the app:
Why can’t I create an Amazon Web Services (AWS) account with my WCM email?
To protect high-risk institutional data (see policy 500.03 - Data Classification), ITS has implemented a policy that prohibits faculty, staff, and students from creating personal AWS accounts with a WCM email address. All institutional data for compute or storage must be stored in a secure environment supported by ITS.
If you are interested in opening a secure AWS account, please submit your request via myHelpdesk.
How long does data migration take?
This varies depending on the service you selected and how much data you have. For example, to migrate data to Managed Hosting, it may take approximately three weeks to set up storage, migrate data, and remove data from the original location. ITS will work with you to plan and schedule your data migration with as little impact to your department as possible.
Can a department transfer data to another storage solution without ITS assistance?
There are some data migrations that can be done by departments, provided they are comfortable transferring the data. However, some data migrations, such as archival transfers, can be complicated, and ITS does not recommend that departments handle this on their own. Reach out to our Data Migration team online using our form for inquiries.
Is there a limit to how much data a department can transfer to a new service?
Data limits are dependent on the service selected. Our technicians will confirm any limits with you during the planning process.
Can ITS support data migration to/from workstation?
No, ITS only supports data migration within the ITS supported storage services.
Can ITS support data migration from Dropbox to Box?
No, ITS does not support data migration from Dropbox. Please refer to the Dropbox site for info on how to transfer files from the platform.

