Last Updated: July 24, 2024
Last Reviewed: July 24, 2024
All members of Weill Cornell Medicine are responsible for protecting the confidentiality, integrity, and availability of data created, received, stored, transmitted, or otherwise used by the college, irrespective of the medium on which the data resides and regardless of format.
In the event the confidentiality, integrity, or availability of data is compromised, and a suspected incident has occurred, the incident should be reported immediately to the Information Technologies & Services Department (ITS) or appropriate compliance office. Reporting incidents quickly—regardless of certainty or magnitude—is critical to ensure the appropriate teams can respond and contain the incident as soon as possible.
Privacy and/or information technology (IT) security incidents can occur at any time and of varying magnitude. Identifying and resolving incidents in an organized systematic way is a vital component of our overarching compliance programs. This policy provides a framework for identifying, assessing, reacting to, communicating about, and documenting an incident along with corresponding remediation plans.
Applies to all members of the Weill Cornell Medicine community who utilize Weill Cornell Medicine information technology resources. This includes Weill Cornell Medicine-Qatar and those responsible for managing and safeguarding Weill Cornell Medicine data.
Security and privacy incidents must be (1) reported, (2) identified, (3) declared, (4) responded to, (5) remediated, and (6) resolved with adequate record-keeping. Detailed requirements for each of these steps are below.
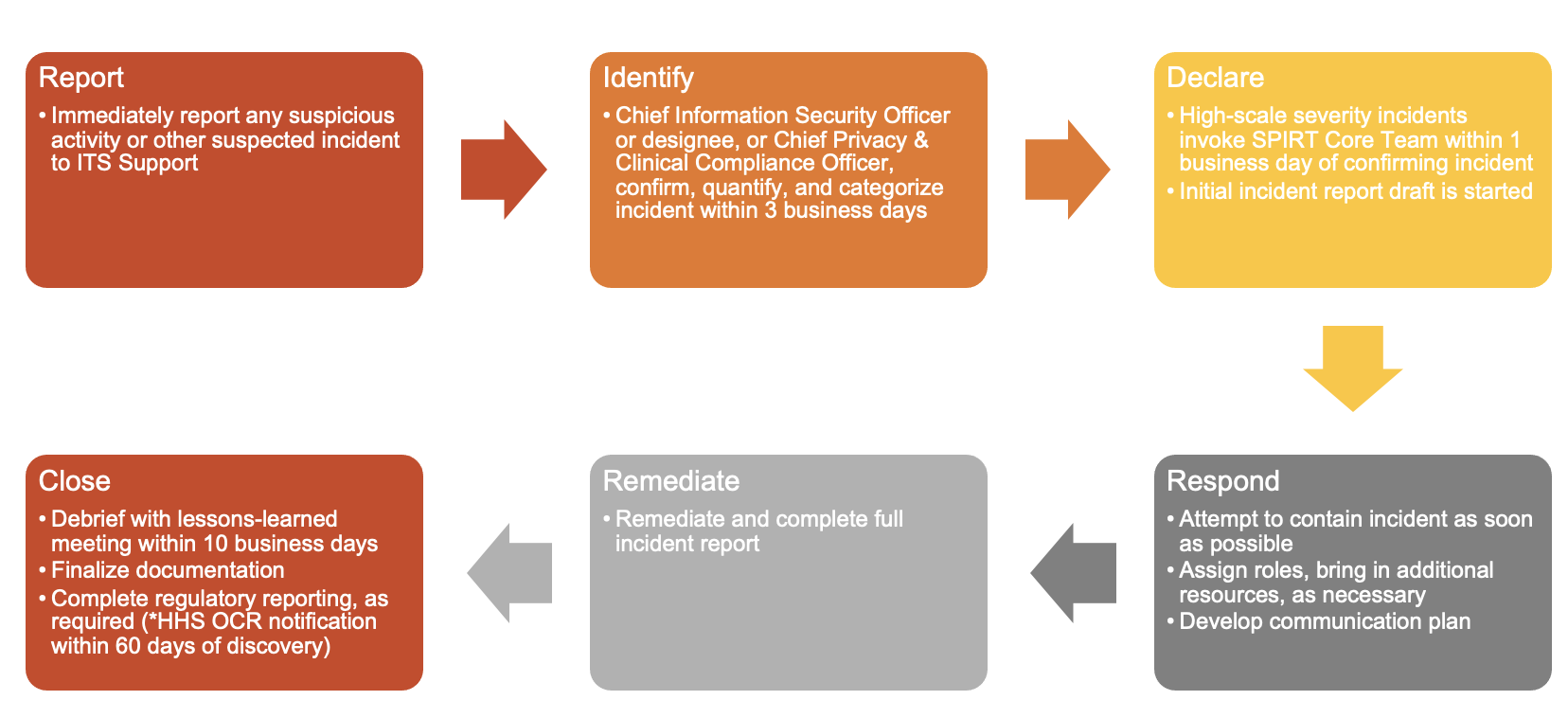
If you know or suspect any unusual or suspicious behavior that does not match your expectation of good security or privacy management, immediately report the incident to ITS Support right away. Even if you are not certain or cannot confirm the incident, it’s imperative that the incident is reported quickly so the right personnel can investigate as soon as possible.
To report an incident, notify ITS Support:
ITS Support
T (212) 746-4878
If you wish to notify a compliance office directly or to report the incident anonymously, the following contacts can be used:
Compliance Office
T (646) 962-7539
Privacy Office
T (646) 962-6930
ITS Security
T (646) 962-3010
Cornell Hotline (Anonymous)
T (866) 293-3077
Filing or reporting an incident can be done without fear or concern of retaliation.
There are many different types of incidents that can be reported to ITS. Examples of incidents include, but are not limited to, the following:
Each reported incident must be investigated. Confirmed incidents will be categorized as follows:
A. Unauthorized or suspicious activity on the Weill Cornell Medicine network, including systems or applicationsAs quickly as possible, reasonable effort must be made to identify the type of data affected by the incident upon discovery and/or declaration. Various regulatory reporting and/or notification requirements, including deadlines, must be adhered to in accordance with applicable state, federal, or regulatory agencies. Such requirements include, but are not limited to, New York State Information Security Breach and Notification Act (ISBANA), Department of Health and Human Services Office of Civil Rights (HHS OCR), Office of Management and Budget Memorandum 07-16 (OMB M-07-16), and the Payment Card Industry Data Security Standard (PCI DSS), including any payment processors for Weill Cornell Medicine. This also includes the evaluation of the state of residence for affected individuals and any applicable reporting authorities.
By means of example, in accordance with OMB M-07-16, when “1) an individual gains logical or physical access without permission to a federal agency network, system, application, data, or other resource; or 2) there is a suspected or confirmed breach of personally identifiable information regardless of the manner in which it might have occurred,” reporting to US-CERT is required within one hour of discovery/detection.
Under the authority of the Chief Information Officer, the Chief Information Security Officer, the Chief Privacy & Clinical Compliance Officer, or their designees can declare a privacy or IT security incident. It is the responsibility of these individuals to evaluate the reported concern using the tools and risk assessment guides expeditiously to determine its authenticity and severity. Severity judgments will be based on ongoing persistent threats, the volume of data involved, and the potential for reputational and/or financial harm to the institution, or any affected individuals.
Low-scale severity incidents will be handled by the ITS Security team or the Compliance & Privacy Office. For more severe incidents, the Chief Information Security Officer or Chief Privacy & Clinical Compliance Officer will convene into a meeting the core members of the Security & Privacy Incident Response Team (SPIRT) and begin drafting the initial incident report. The initial details of the incident will be discussed with the SPIRT core team at this time.
The primary purpose of SPIRT is to determine and guide the college’s response to an IT security or privacy incident, up to and including the need to satisfy existing data breach notification statutes or processes as well as an institutional decision to notify individuals of a breach of their personally identifiable or protected health information.
The SPIRT core team members include:
As warranted by the type and scale of the incident, any of the SPIRT virtual team members may be convened by a core team member based on the type and scope of incident. Virtual team members provide assistance, advisement, and expertise from their representative areas. The SPIRT virtual team members include:
Other individuals not on the SPIRT core or virtual teams may be convened by a core team member based on the incident. Such individuals may include, but are not limited to, department administrators or subject matter experts.
Once an incident has been reported and declared, the incident must be contained to prevent further harm. By means of example, the following containment steps may be taken:
Effective containment stops damage from being done and allows assessment of the scope of the incident and the initiation of remediation activities.
Upon declaring the incident, the SPIRT core team members may convene the appropriate virtual team members—including any additional resources necessary, such as storage facilities, out-of-band communication channels, or additional staff—and assign roles pertaining to the incident assessment and response:
The incident commander is responsible for coordinating all stages of the incident response process and specifically acts as the leader of the investigation. In addition, the incident commander has the following duties:
The incident coordinator is responsible for the oversight of the incident response, including, but not limited to, the following duties:
The IT forensics investigator is responsible for the electronic discovery of data from in-scope systems, applications, or logs. Other duties may include:
The data analysis investigator is responsible for reviewing all aggregated documents, forms, transcripts, and other relevant materials. In addition, the data analysis investigator is responsible for the following duties:
The communications coordinator must be prepared to respond to any authorized/approved party at any time throughout the incident. Responsibilities include:
In order to limit exposure and maintain confidentiality about the incident, limited information pertaining to the incident should be disclosed upon initial notification (e.g., type/category of incident, date occurred, reported by, etc.). An “informed parties” log may be kept documenting the degree and reason to which all parties have been informed about the incident.
Throughout all communications, the incident responders should be reminded of the confidentiality of the incident and that information must not be shared outside the response team unless warranted.
The initial incident report must be presented and reviewed at the convening of the SPIRT core team. The SPIRT data analysis investigator is responsible for compiling the data elements below as part of the incident response procedures. Appropriate templates are available based on the type of incident. Distribution and review of the working draft is restricted and must be conducted under privilege with a member of the Office of General Counsel included on any distribution list or at the review sessions. The incident report must contain the following attributes:
Throughout the incident response process, all items should be completed, when known, before the report can be finalized.
1 The action log must include all actions taken in chronological order, along with communications made and the indexing of any potential threats found, pertinent discoveries made, or potential data involved throughout the process.
2 The remediation plan should eliminate, mitigate, or document acceptance of the threats discovered in the incident and any actions to address these items going forward.
3 The communications plan must include the timing, preparation, revision, acceptance, and delivery of internal communications (e.g., executive committees, faculty, staff, students, affiliate institutions, etc.) and external communications (e.g., media, website, letters to affected individuals, etc.).
4 Regulatory reporting and/or notification requirements, including deadlines, must be adhered to in accordance with applicable state, federal, or regulatory agencies (as described in 3.01 Identifying Affected Data).
Closing an incident indicates that the incident has been completely contained, remediated, and properly reported. In order to close an incident, all attributes in the incident report must be completed, as defined in Incident Report.
Incidents can only be closed by consensus of the SPIRT core team.
All documentation and evidence pertaining to the incident must be stored in a secure location approved by the Office of General Counsel. A paper copy of the incident report should be provided to and retained by the Office of General Counsel. The data analysis investigator should ensure that all documentation is organized in a clear, cohesive manner. It is important to note that additional activities may occur after the incident has been closed, such as responding to requests for additional information from regulatory agencies. These activities need to be memorialized and added to the documentation repository. Additionally, the SPIRT core team should be notified of any new developments, including regulatory inquiries, to closed incidents.
A post-mortem meeting should be held within ten business days to review the incident and adherence to this policy for any future modifications. An independent reviewer may be engaged to provide additional feedback on the incident handling procedures and records.
All WCM Workforce Members are responsible for adhering to this policy. Failure to comply will be evaluated on a case-by-case basis and could lead to corrective action, up to and including termination, consistent with other relevant WCM and University Policies. Instances of non-compliance that potentially involve a lapse of professionalism may lead to engagement of the Office of Professionalism for evaluation and intervention.
Direct any questions about this policy, 500.05 – Security and Privacy Incident Response Plan, to the Chief Information Security Officer, using one of the methods below: