What is Two-Factor Authentication?
Two-Factor Authentication is a security best practice that requires more than one type of security method when logging in to an application. An authentication method can include something you know (a password or PIN), or something you have (a unique code).
Two-Factor Authentication adds an extra layer of protection that makes it more difficult for anyone to gain access to your accounts, even if your password has been compromised.
The Exit button doesn’t work. How do I log out of WRG?
You can log out of WRG by closing your browser window.
What if I’m the Principal Investigator on a project for which I’m submitting a Study Specific Report (SSR)?
Select your own name from the dropdown menu.
One of my submissions was returned to me requesting more information. Where do I respond?
Click the folder icon in the top left corner of the Action Item. Respond in the comments section of the form.
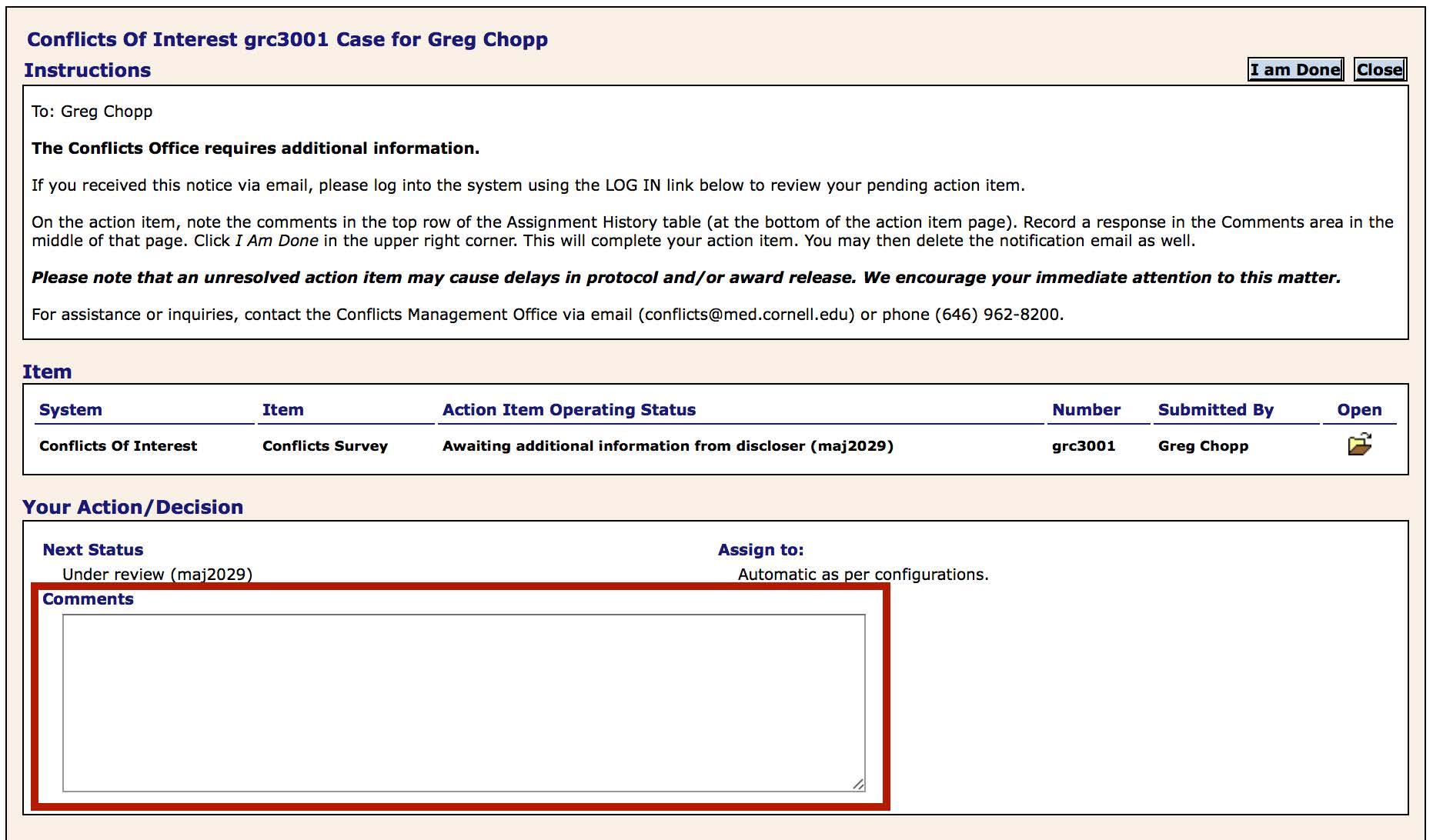
I see I have an Open Action Item. How do I view more details?
If a submission is returned to you, you will see an Open Action Item on first page after login. Click the folder icon to view that action item.
![]()
How do I know if my submission in WRG was successfully received?
You will receive an email confirmation. You will also receive a notification if any action needs to be taken on your submission.
What do I do if I'm having trouble finishing my transaction in WRG?
In many cases, the Completed checkbox must be checked before clicking Submit. If this doesn’t work, there may be required fields that are not filled out. Review the form your submitting and check for any errors or missed fields.
If you continue to experience issues, contact the Service Desk.